Configuring the authentication type for SSH keys
Describes the procedure to configure the authentication type for SSH Keys
The Secure Shell (SSH) is a network protocol that ensures an secure communication over unsecured network. A user connects to the SSH server using the SSH Client. The SSH protocol is comprised of a suite of utilities which provides high-level authentication encryption over unsecured communication channels.
A typical SSH setup consists of a host machine and a remote machine. A key pair is required to connect to the host machine through any remote machine. A key pair consists of a Public key and a Private key. The key pair allows the host machine to securely connect to the remote machine without entering a password for authentication.
For enhancing security, a Private key is secured using a passphrase. This ensures that only the rightful recipient can have access to the decrypted data. You can either generate key pairs or work with existing key pairs.
If you add a Private key without a passphrase, it is encrypted with a random passphrase. This passphrase is scrambled and stored.
If you choose a Private key with a passphrase, then the Private key is stored as it is. This passphrase is scrambled and stored.
For more information about generating the SSH key pairs, refer Adding a New Key.
The SSH protocol allows an authorized user to connect to the host machines from the remote machines. Both inbound communication and outbound communication are supported using the SSH protocol. An authorized user is a combination of an appliance user associated with a valid key pair. An authorized user must be listed as a valid recipient to connect using the SSH protocol.
The SSH protocol allows the authorized users to run tasks securely on the remote machine. When the users connect to the appliance using the SSH protocol, then the communication is known as inbound communication.
For more information about inbound SSH configuration, refer here.
When the users connect to a known host using their private keys, then the communication is known as outbound communication. The authorized users are allowed to initiate the SSH communication from the host.
For more information about outbound SSH configuration, refer here.
On the ESA Web UI, you can configure all the following standard aspects of SSH:
SSH pane:With the SSH configuration Manager you can examine and manage the SSH configuration. The SSH keys can be configured in the Authentication Configuration pane on the ESA Web UI.
The following figure shows the SSH Configuration Manager pane.
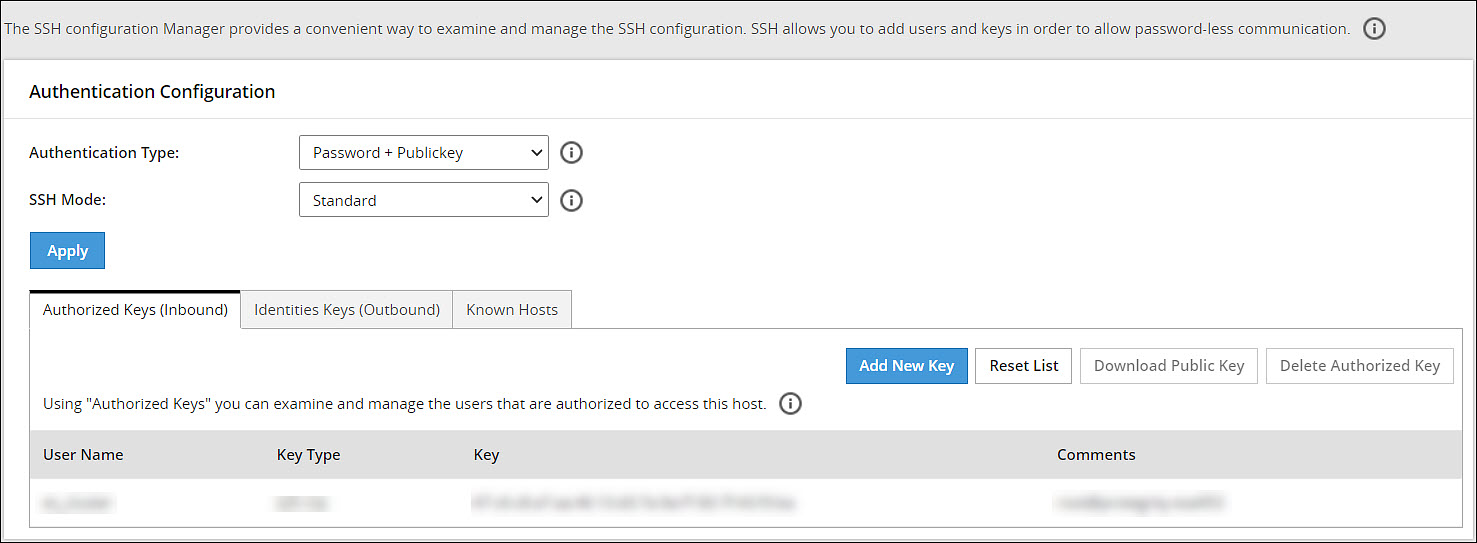
Authentication Type:The SSH Server is configured in the following three ways:
| Authentication Type | Description |
|---|---|
| Password | In this authentication type, only the password is required for authentication to the SSH server. The public key is not required on the server for authentication. |
| Public Key | In this authentication type, the server requires only the public key for authentication. The password is not required for authentication. |
| Password + Public key | In this authentication type, the server can accept both, the keys and the password, for authentication. |
SSH Mode:
From the Web UI, navigate to Settings > Network > SSH. Using the SSH mode, restrictions for SSH connections can be set. The restrictions can be hardened or loosened based on the needs. There are four modes SSH mode types are shown below.
| Mode | SSH Server | SSH Client |
|---|---|---|
| Paranoid | Disable root access | Disable password authentication, that is, allow to connect only using public keys. Block connections to unknown hosts. |
| Standard | Disable root access | Allow password authentication. Allow connections to new (unknown) hosts, enforce SSH fingerprint of known hosts. |
| Open | Allow root access Accept connections using passwords and public keys. | Allow password authentication. Allow connection to all hosts – do not check hosts fingerprints. |
Describes the procedure to configure the authentication type for SSH Keys
Describes the procedure to configure the inbound communication for SSH Keys
Describes the procedure to configure the outbound communication for SSH Keys
Describes the procedure to configure the known hosts for SSH Keys