Protegrity Gateway Technology
Protegrity Gateway Technology provides an insight into the gateway technology offered that lets you protect data at rest as well as on the fly.
Background
The most important asset for organizations today is data. Data is being collected at an unprecedented rate. Data analysts and data mining scientists develop analytical processes to gain transformative insights from the collected data to gain corporate advantages, growth, and innovation.
This rich pool of data is commonly tied to individuals, such as employees, customers, patients, and the like, making it a target for identity theft. The ever-increasing cases of data breaches is a proof that the business of stealing data is a large and lucrative business for hackers. In effort to stop data thefts, organizations are constantly looking for innovative solutions for protecting sensitive data without affecting the use and analysis of this data.
Audience
Multiple stakeholders collaborate to deliver enterprise level data security solutions. Some are responsible for setting corporate business requirements while others own the responsibility of designing and implementing data security solutions.
The audience for this document is the following stakeholders who play a role in the data security ecosystem:
Business Owners: Focused on maximizing the value and growth delivered by their business system. Data security concerns and security solutions may prevent business owners from executing their plans. These stakeholders are the advocate for the data and its untapped potential.
Security Professionals (CISO, Security Officers, Governance, Risk, etc.): Responsible for keeping business systems secure. They must understand the goals of the business owners and design and deliver data security solutions that offer a balance between protecting the data and enabling business usage. These security professionals:
- Set the security risk tolerance for the organization.
- Identify the data that is deemed sensitive in an organization.
- Design and implement the data security solution that meets business requirements.
- Establish the ongoing monitoring and alerting of sensitive data.
IT (DBA’s, Developers, etc.): Responsible for implementing and deploying business and data security solution. Some organizations have a specialized IT team that is part of the security organization. In this document, this team is identified as the team that implements and deploys the data security solution, irrespective of their location in the organization chart.
System Architects: Equipped with deep knowledge of business infrastructure and of the corporate data security requirements makes them the center authority responsible for the technical architecture of the data security solution.
These stakeholders are involved from the initial stages of vetting data security vendors to the eventual design of the data security architecture implemented by the IT stakeholders.
What is Protegrity Gateway Technology
Protegrity Gateway Technology is an umbrella term for the new and innovative push to deliver data security solutions from Protegrity that is highly transparent to corporate infrastructures.
When adopting data security solutions, companies expect minimal impact on existing business systems and processes. In the past, data security solutions have been integrated into business applications and databases.
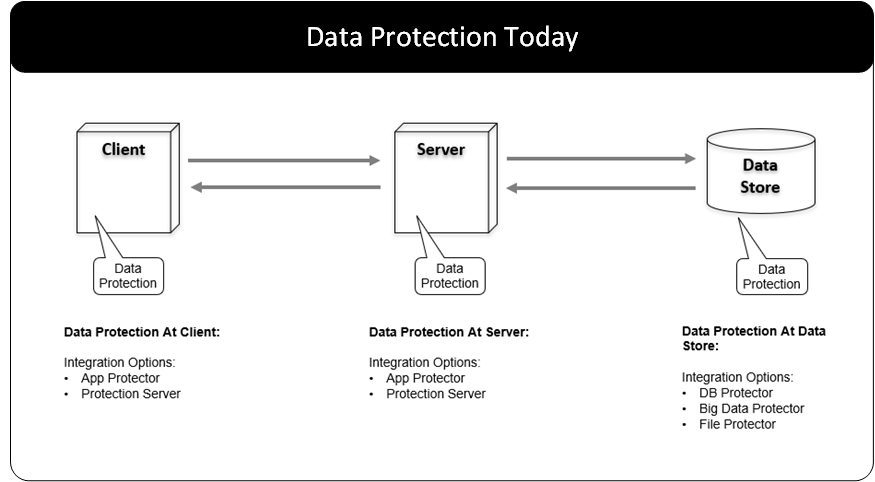
These approaches require changes to these systems.
The gateway is a network intermediary between systems that communicate with each other through the network. By delivering data security solutions on the network, changes to the existing systems are avoided or minimized.
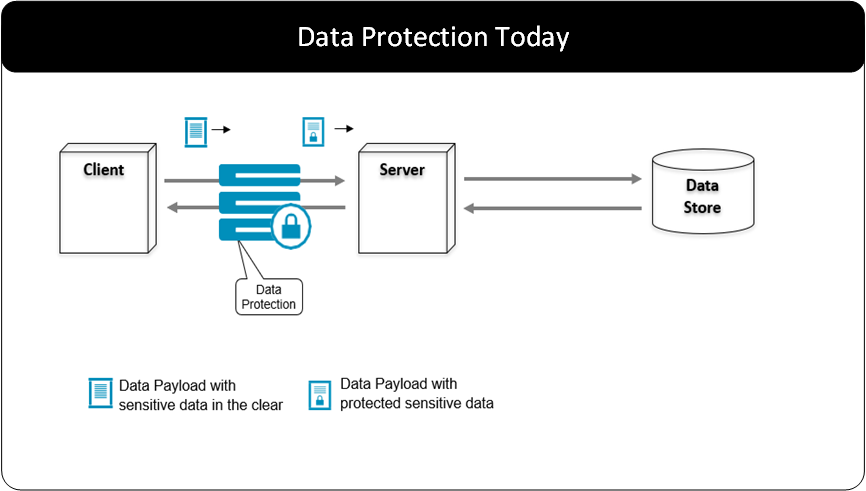
The Protegrity Gateway Technology protects data on the network.
Why the Protegrity gateway technology?
The Protegrity Gateway Technology represents an extension to the Protegrity Data-Centric Audit and Protection (DCAP) platform and Protegrity Vaultless Tokenization. The largest enterprises worldwide are using these today to protect sensitive data.
The combination of the Protegrity DCAP platform, Protegrity Vaultless Tokenization, and the Protegrity Gateway Technology delivers many benefits:
Enterprise: As yet another protector in the Protegrity Data Centric Audit and Protection platform family, the Protegrity Gateways can receive and use policies from the Enterprise Security Administrator (ESA). It define rules for how you want to protect sensitive data throughout your enterprise. The protected data is interoperable with other protectors in the DCAP family.
Transparent: Delivering data protection on the network eliminates the need to modify the source or destination systems. This makes the implementation of a security solution easier than if you had to modify application code or database schema.
Fast: The gateway provides the fastest mechanism to protect and unprotect data at line speed. The granularity of the security operations is very high since the operations are applied very close to the data with no latency.
Scalability: The gateways can scale vertically as well as horizontally. The vertical scaling is enabled through the addition of CPU and RAM while horizontal scaling is enabled by adding more nodes to a gateway cluster.
Configuration over Programming (CoP): The implementation of data security with the Protegrity Gateways does not require programming. Implementation is configured through an easy to use web interface. This practice is called Configuration over Programming (CoP).
Deployment Flexibility: The Protegrity Gateways as well as the Protegrity DCAP platform can be deployed on-premise, in the cloud deployment, or in a hybrid deployment architecture.
Use Cases: The Protegrity Gateway Technology is a kind of “Swiss Army Knife” for applying data security across many use cases that are described in detailed in this document.
Extensibility: While CoP delivers virtually all you need to implement data security solutions using the Protegrity Gateways, you may extend the functionality using Python programming language through User Defined Functions.
SaaS Protection Agility: SaaS applications (Salesforce, Workday, Box, etc.) have gained popularity due to the ease with which you can add business functionality to your organization. Because of their cloud-based deployment model, SaaS applications can change quickly. The approach of implementing data security solutions with Configuration over Programming (CoP) makes it easy to keep up with these changes and avoid outages.
How Protegrity gateway protects data
Protegrity gateways deliver security operations on sensitive data by peering into the payloads that are being transmitted through the network.
The gateway intercepts standard protocols such as TCP/IP. The payloads on the backs of these protocols are scanned for sensitive data and security operations (protection or un-protection) are applied to the sensitive data as it passes through the gateway.
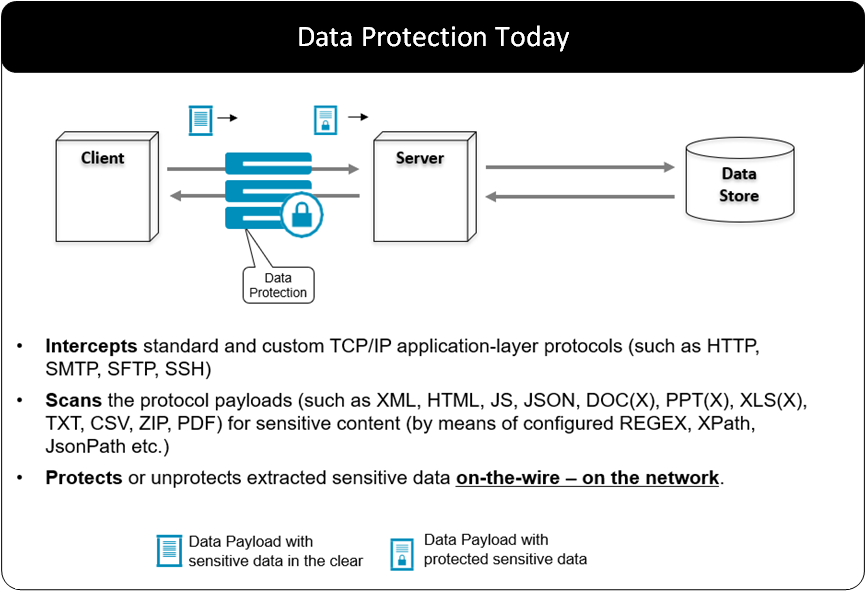
With the gateway approach to delivering security operations, impact to existing systems is eliminated or minimized.
Data-centric auditing and protection platform
Protegrity Gateway Technology is part of the Protegrity Data-Centric Audit and Protection family of protector. Protegrity Gateway Technology together with the Enterprise Security Administrator (ESA) makes up the Protegrity Data-Centric Audit and Protection Platform.
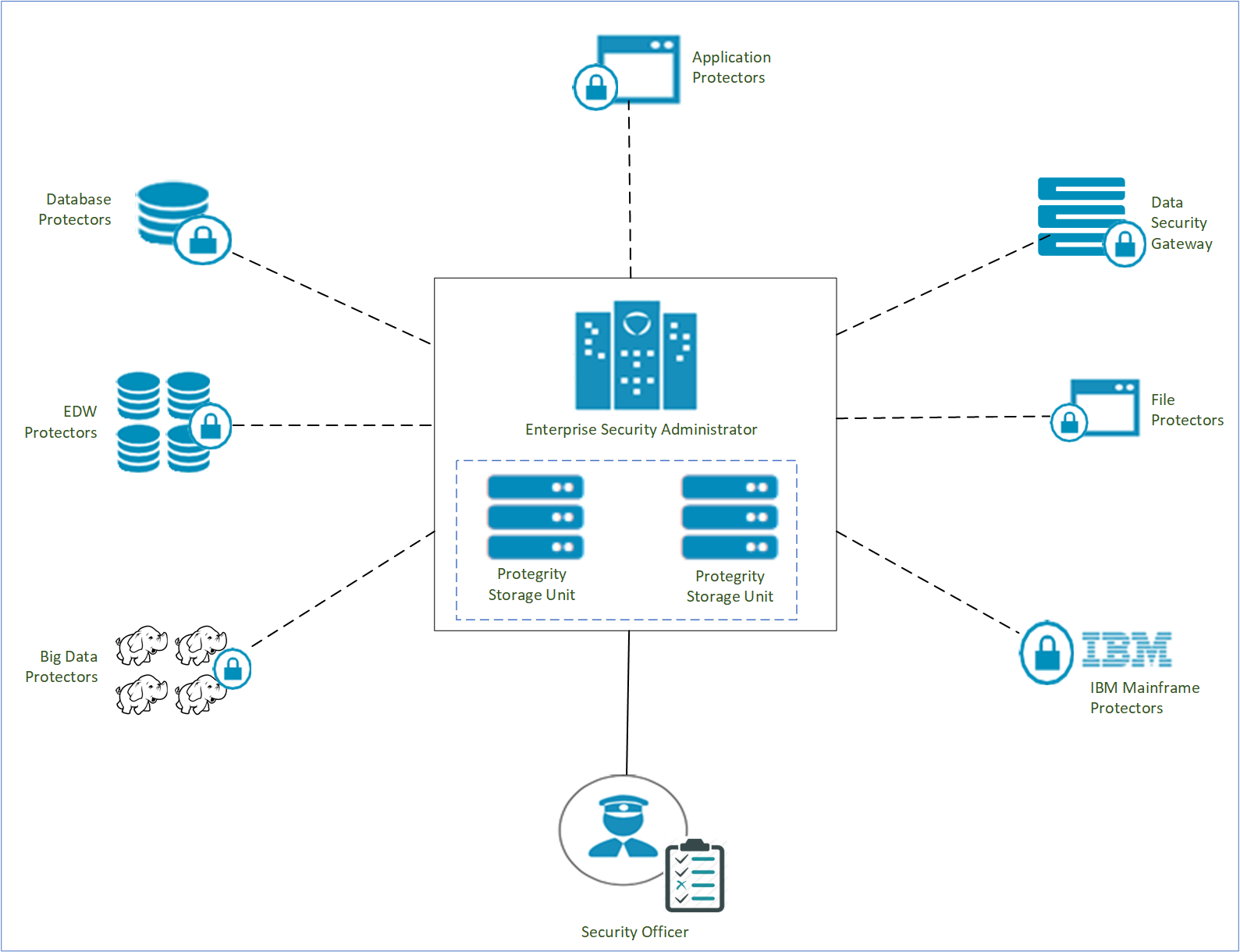
The Enterprise Security Administrator (ESA) is a central point of management of data security policies enforced by various protectors. Each protector is designed to accept an ESA policy that provide the rules for protecting and unprotecting sensitive data.
Security operations on sensitive data performed by any of the protectors can be audited. Audit logs based on invoked security operations are sent back to ESA for reporting and alerting purposes.
You can protect sensitive data in any business system that is secured with Protegrity. It allows the protected data to travel in a protected state between different business systems, and then unprotect it in a target system for authorized users.
Fine Grained and Coarse Grained Data Security:
Data Security can span many different types of security that are differentiated by based on the point where security policies are applied. Security can be applied to the perimeter by only letting some users in.
Security applied to data can be delivered in the following forms:
It can be applied to the data as an access control layer by hiding data from un-authorized users.
It can be applied to data by encrypting the raw storage associated with data stores. This is sometimes called coarse grained data protection or tablespace protection or Transparent Database Encryption.
It can also be applied to the specific data itself with encryption or tokenization such as the Social Security Number, the E-mail address, the Name and so on.
Protegrity Vaultless Tokenization enables you to reduce the scope of systems where sensitive data exists in the clear, with minimum to no impact of its business usage.
Together with other protectors contained in the Protegrity Data-Centric Audit and Protection platform, the Protegrity Gateway Technology products deliver on these approaches with a single product.
Configuration over Programming (CoP) brings it all together
The Protegrity Gateway Technology brings together the ability to peer into networks payloads and the security policy-based rules for protecting sensitive data with a concept called Configuration over Programming (CoP).
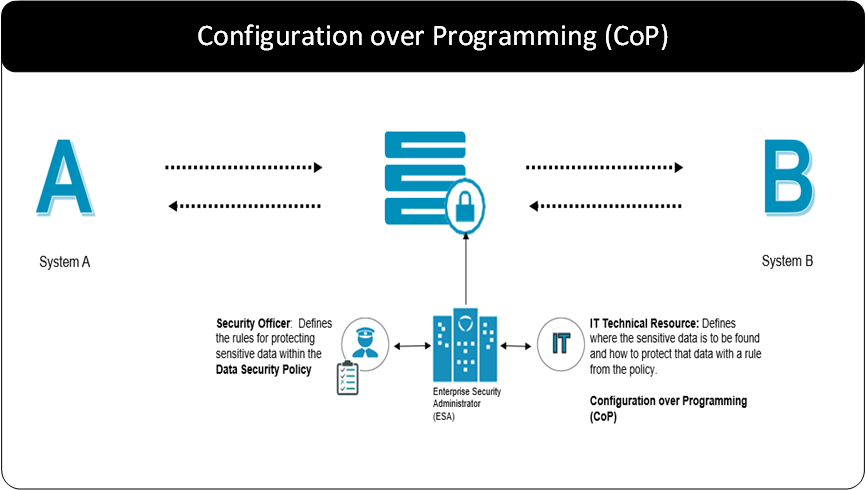
The diagram above depicts the gateway along with the components that together constitute CoP. Data is transmitted bidirectional between System A and System B. The gateway acts as a network intermediary through which the transmissions pass. A set of rules called CoP Profiles define the transformations performed on that data.
Security Officers set rules that define how the security team would like corporate security solutions to treat sensitive data. Having the security team define these rules across the corporate data asset delivers consistency in the security treatment. This helps both security and the usability of the data. Having the security team responsible for this task also delivers separation of duties. This helps to reduce or eliminate a conflict of interest in who sets the rules for protecting sensitive data and who can see the sensitive data in the clear.
IT technical resources bring it all together through CoP. CoP enables a technical resource, a CoP Administrator, to create a set of CoP profiles that blend the different aspects of delivering security or other transformations on data. A CoP Profile include:
Data Collection: The data collection profile rules define the network protocols that are being inspected. For example, you can instruct the gateway that it will inspect HTTP or SFTP. These are standard protocols on top of which the transmission of data across networks are built.
Extend Gateway: If you have a custom protocol, the gateway can be extended and configured to accept that as well.
Data Extraction: Protocols carry many kinds of payloads that are commonly used. They carry web pages or document content that are used to transfer business system data from one application to another. CoP Profiles are configured to identify specific data within these commonly used payloads.
Extend Codecs: A set of extraction codecs are included with the gateway. s with the protocols, the data extraction codecs can also be extended to include new standard or custom codecs.
Actions on Data: Once you have defined the protocol and identified specific data within a payload, you can then apply an action or a transformation rule on the data. In the context to data security, this action is a security operation (protect or unprotect). The rules for performing the security action come from the policy rules identified by the security team.