SMTP Tunnel
The DSG can perform data security operations on the sensitive data sent by an Simple Mail Transfer Protocol (SMTP) client before the data reaches the destination SMTP server.
Over the internet, SMTP is an Internet standard for sending emails. When an email is sent to anyone, the email is sent using an SMTP client to the SMTP server. For example, if an email is sent from john.doe@xyz.com to jane.smith@abc.com, the email first reaches the xyz’s SMTP server, then reaches abc’s SMTP server, before it finally reaches the recipient, jane.smith@abc.com.
The DSG intercepts the communication between the SMTP client and server and performs data security operations on sensitive data. The sensitive data residing in the email elements, such as subject of an email, body of an email, attachments, filename, and so on, are supported for the SMTP protocol:
When the DSG is used as an SMTP gateway, the Rulesets must use the SMTP service and the first child Extract rule must be SMTP Message.
The following image illustrates how the SMTP protocol is handled in the DSG. Consider an example where, john.doe@xyz.com is sending an email to jane.smith@xyz.com. The xyz SMTP server is the same for the sender and the recipient.
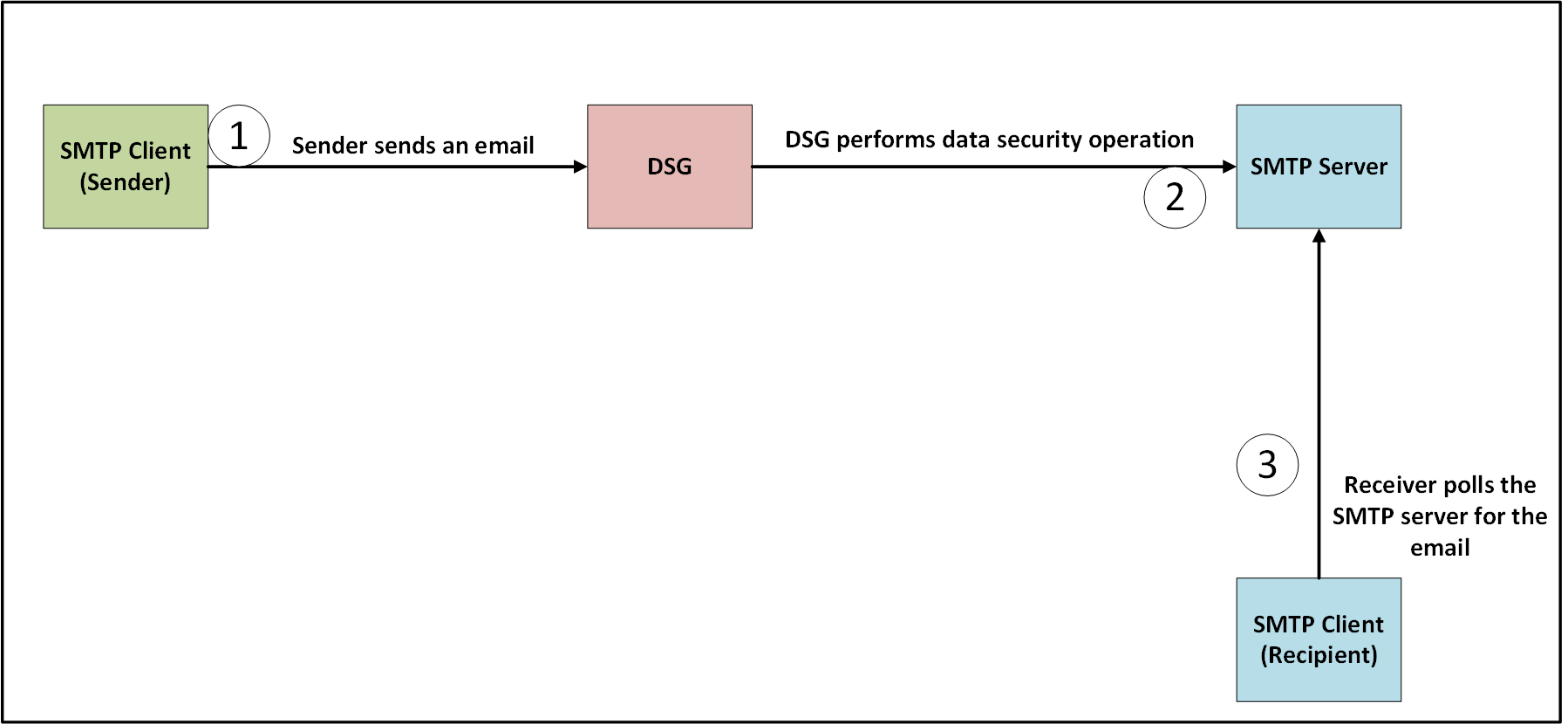
The sender,
john.doe@xyz.com, sends an email to the recipient,jane.smith@xyz.com. The Subject of the email contains sensitive data that must be protected before it reaches the recipient.The DSG is configured with an SMTP tunnel such that it listens for incoming requests on the listening ports. The DSG is also configured with Rulesets such that an Extract rule extracts the Subject from the request. The Extract rule also defines a regex that extracts the sensitive data and passes it to the Transform rule. The Transform rule performs data security operations on the sensitive data.
The DSG forwards the email with the protected data in the Subject to the SMTP server.
The recipient SMTP client polls the SMTP server for any emails. The email is received and the sensitive data in the Subject appears protected.
The following image illustrates the settings specific to the SMTP protocol.
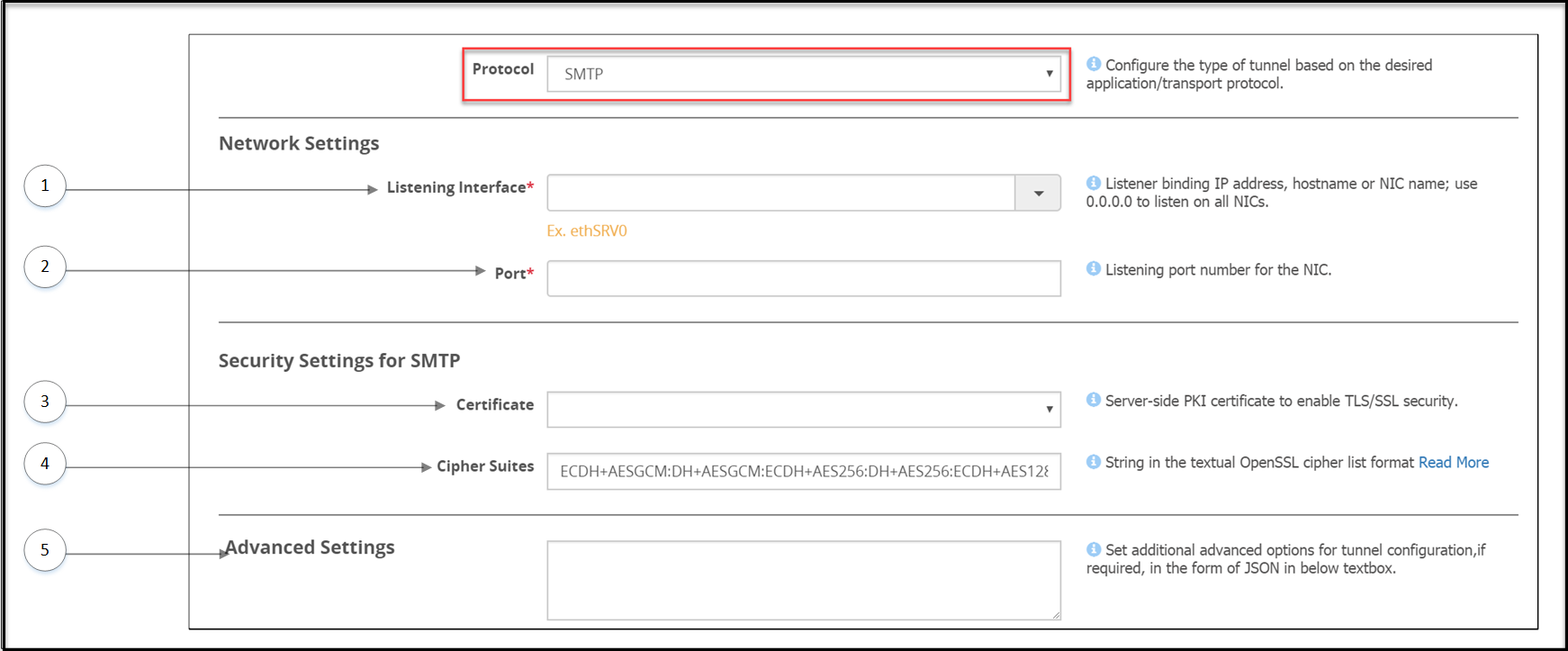
The options specific to the SMTP Tunnel are described in the following table.
| Callout | Column/Textbox/Button | Description | Notes |
|---|---|---|---|
| Network Settings | |||
| 1 | Listening Interface* | Enter the service IP of the DSG, where the DSG listens for the incoming SMTP requests. | |
| 2 | Port | Port linked to the listening address. | |
| Security Settings for SMTP | |||
| 3 | Certificate | Server-side Public Key Infrastructure (PKI) certificate to enable TLS/SSL security. | |
| 4 | Cipher Suites | Semi-colon separated list of Ciphers. | |
| 5 | Advanced Settings | Set additional advanced options for tunnel configuration, if required, in the form of JSON. | In a scenario where an ESA and two DSG nodes are in a cluster, by using the Selective Tunnel Loading functionality, you can load specific tunnel configurations on specific DSG nodes. |
The ssl_options supported for the SMTP Tunnel are described in the following table.
| Options | Description | Default |
|---|---|---|
| cert_reqs | Specifies whether a certificate is required for validating the SSL connection between the SMTP client and the DSG. The following integer or string values can be configured:
| 0 or CERT_NONE |
| ssl_version | Specifies the SSL protocol version used for establishing the SSL connection between the SMTP client and the DSG. | PROTOCOL_SSLv23 |
| ca_certs | Path where the CA certificates (in PEM format only) are stored. | n/a |
* The following Listening Interface options are available:
- ethMNG: The management interface on which the DSG Web UI is accessible.
- ethSRV0: The service interface where the DSG listens for the incoming SMTP requests.
- 127.0.0.1: The local loopback adapter.
- 0.0.0.0: The broadcast address for listening to all the available network interfaces.
- Other: Manually add a listening address based on your requirements.
**-The advanced settings that can be configured for SMTP Protocol.
| Options | Description | Default (if any) |
|---|---|---|
| idle_connection_timeout | Timeout set for an idle connection.The datatype for this option is seconds. | 30 |
| default_window_size | SSH Transport window size | 2097152 |
| default_max_packet_size | Maximum packet transmission in the network. The datatype for this option is bytes. | 32768 |