Post upgrade steps
Before you begin
If only two ESAs are available in the Audit Store cluster, then remove the secondary ESA from the cluster, upgrade the primary ESA, upgrade the secondary ESA, and add the secondary ESA to the cluster. However, a minimum of three ESAs are recommended for the Audit Store cluster.
Upgrade each ESA to v10.0.x. After upgrading all the ESA appliances, add the ESA appliances to the TAC, and then create the scheduled tasks.
Installing the DSG patch on ESA
If you install the DSG v3.3.0.0 patch on the ESA v10.0.x, then perform the following operations:
Run the Docker commands
- On the ESA CLI Manager, navigate to Administration > OS Console.
- Run the
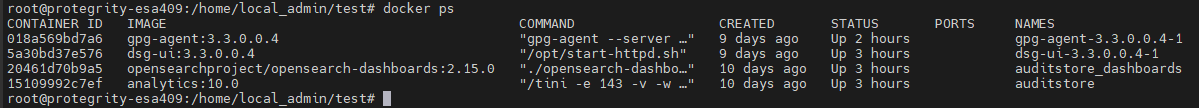
docker pscommand. A list of all the available docker containers are displayed as shown in the following example:
Run the below commands to update the container configuration.
docker update --restart=unless-stopped --cpus 2 --memory 1g --memory-swap 1.5g dsg-ui-3.3.0.0.5-1docker update --restart=always --cpus 1 --memory .5g --memory-swap .6g gpg-agent-3.3.0.0.5-1
The values of--cpus,--memory, and--memory-swapcan be changed as per the requirements.
Update the evasive configuration file
- On the ESA CLI Manager, navigate to Administration > OS Console.
- Add new mod evasive configuration file using the following command.
nano /etc/apache2/mods-enabled/whitelist_evasive.conf - Add the following parameters to the mod evasive configuration file.
<IfModule mod_evasive20.c>
DOSWhitelist 127.0.0.1
</IfModule>
- Save the changes.
- Set the required permissions for evasive configuration file using the following command.
chmod 644 /etc/apache2/mods-enabled/whitelist_evasive.conf - Reload the apache service using the following command.
/etc/init.d/apache2 reload
Verifying Upgrade Logs
During the upgrade process, logs describing the status of the upgrade process are generated. The logs describe the services that are initiated, restarted, or the errors generated.
To view the logs under the /var/log directory from the CLI Manager, navigate to CLI Manager > Administration > OS console.
- patch_ESA_<version>.log - Provides the logs for the upgrade.
- syslog - Provides collective information about the syslogs.
Enabling Rollover Index Task
Perform the following steps to enable Rollover Index task:
Log in to the ESA Web UI on any of the nodes in the Audit Store cluster.
Navigate to Audit Store > Analytics > Scheduler
Click Enable for the Rollover Index task. The slider moves to the on position that is blue in color.
Enter the root password and click Submit, to apply the updates.
Enabling the Audit Store Management - Cluster Config - Sync task
Enable the Audit Store Management - Cluster Config - Sync task on all nodes after upgrading all the ESAs.
Log in to the ESA Web UI.
Navigate to System > Task Scheduler.
Click the Audit Store Management - Cluster Config - Sync task and click Edit.
Select the Enable check box for the Audit Store Management - Cluster Config - Sync task.
Click Save and then click Apply after performing the required changes.
Enter the root password and select OK.
Repeat the steps on all the nodes in the Audit Store cluster.
Joining nodes in ESA cluster
Perform this step only after upgrading all the ESA appliances.
To add the ESAs in a TAC setup using the ESA Web UI:
- From the primary ESA, create a TAC.
- Join all secondary ESAs one-by-one in the TAC.
Creating a Cluster Scheduled Task
Ensure to create a cluster scheduled task, only after upgrading all the ESA appliances.
Perform the following steps to create a cluster scheduled task:
From the ESA Web UI, navigate to System > Backup & Restore > Export.
Under Export, select the Cluster Export radio button.
Click Start Wizard.
The Wizard - Export Cluster screen appears.
In the Data to import, customize the items that you need to export from this machine and imported to the cluster nodes.
If the configurations must be exported on a different ESA, then clear the Certificates check box. If you import the ESA Management and WebService Certificates from a different node in the cluster, then rotate the Insight certificates after the import is complete. For rotating the Insight certificates, use the steps from Rotating Insight certificates.
Click Next.
In the Source Cluster Nodes, select the nodes that will run this task.
You can specify them by label or select individual nodes.
Click Next.
In the Target Cluster Nodes, select the nodes to import the data.
Click Review.
The New Task screen appears.
Enter the required information in the following sections.
- Basic Properties
- Frequencies
- Restriction
- Logging
Click Save.
A new scheduled task is created.Click Apply to apply the modifications to the task.
A dialog box to enter the root user password appears.Enter the root password and click OK.
The scheduled task is operational.Click Run Now to run the scheduled task immediately.
Optional Restoring the Configuration for the External SIEM
If an external SIEM is used and logs are forwarded to the external SIEM, perform the following steps to restore the configuration:
From the CLI Manager of the Primary ESA, perform the following steps.
Log in to the CLI Manager of the Primary ESA.
Navigate to Administration > OS Console.
Enter the root password and select OK.
Update the configuration files.
Navigate to the config.d directory.
cd /opt/protegrity/td-agent/config.dIdentify the hostname of the machine.
- Open the OUTPUT.conf file using a text editor.
- Locate the hosts parameter in the file.
- Make a note of the hosts configuration value.
- Close the file.
Back up the existing OUTPUT.conf file.
mv OUTPUT.conf OUTPUT.conf_from_<build_number>The system uses the .conf extension. To avoid configuration conflicts, ensure that the backup file name is appended to the file name extension, for example, .conf_backup or .conf_bkup123.
Open the backup file that is created during the upgrade using a text editor.
Obtain the build number from the readme file that is provided with the upgrade patch.
The system uses the .conf extension. To avoid configuration conflicts, ensure that the backup file name is appended to the file name extension, for example, .conf_backup or .conf_bkup123.Update hosts localhost to the hosts configuration value identified from the OUTPUT.conf file in the earlier step.
The extract of the updated file is shown in the following example.
<existing code> . . hosts protegrity-esa123.protegrity.com . . .<exising code>Save and close the file.
Rename the configuration file to OUTPUT.conf.
mv OUTPUT.conf.before_<build_number> OUTPUT.conf
Restart the td-agent service.
Log in to the ESA Web UI.
Navigate to System > Services > Misc > td-agent,
Restart the td-agent service.
Repeat these steps on all the ESAs where the external SIEM configuration was updated before the upgrade.