Working with the Protegrity LDAP Server
Every appliance includes an internal directory service. This service can be utilized by other appliances for user authentication.
For example, a DSG instance might utilize the ESA LDAP for user authentication. In such cases, you can configure the LDAP settings of the DSG in the Protegrity LDAP Server screen. In this screen, you can specify the IP address of the ESA with which you want to connect.
You can add IP addresses of multiple appliances to enable fault tolerance. In this case, if connection to the first appliance fails, connection is transferred to next appliance in the list.
If you are adding multiple appliances in the LDAP URI, ensure that the values of the Bind DN, Bind Password, and Base DN is same for all the appliances in the list.
To specify Protegrity LDAP server:
Login to the Appliance CLI Manager.
Navigate to Administration > Specify LDAP Server.
Enter the root password and select OK.
In the LDAP Server Type screen, select Protegrity LDAP Server and select OK.
The following screen appears.
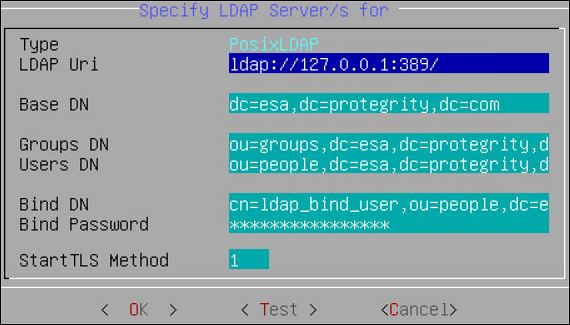
Enter information for the following fields.
Table 1. LDAP Server Settings
Setting Description LDAP URI Specify the IP address of the LDAP server you want to connect to in the following format. ldap://host:port. You can configure to connect Protegrity Appliance LDAP. For example,ldap://192.168.3.179:389.For local LDAP, enter the following IP address:ldap://127.0.0.1:389.If you specify multiple appliances, ensure that the IP addresses are separated by the space character.For example,ldap://192.1.1.1 ldap://10.1.0.0 ldap://127.0.0.1:389Base DN The LDAP Server Base distinguished name. For example: ESA LDAP Base DN: dc=esa,dc=protegrity,dc=com.Group DN Distinguished name of the LDAP Server group container. For example: ESA LDAP Group DN:ou=groups,dc=esa,dc=protegrity,dc=com.Users DN Distinguished name of the user container. For example: ESA LDAP Users DN:ou=people,dc=esa,dc=protegrity,dc=com.Bind DN Distinguished name of the LDAP Bind User. For example: ESA LDAP Bind User DN cn=admin, ou=people, dc=esa, dc=protegrity, dc=com.Bind Password The password of the specified LDAP Bind User. If you modify the bind user password, ensure that you use the Specify LDAP Server tool to update the changes in the internal LDAP.Bind UserThe bind user account password allows you to specify the user credentials used for LDAP communication. This user should have full read access to the LDAP entries in order to obtain accounts/groups/permissions.If you are using the internal LDAP, and you change the bind username/password, using Change a directory account option, then you must update the actual LDAP user. Make sure that a user with the specified username/password exists. Run Specify LDAP Server tool with the new password to update all the products with the new password. Refer to section Protegrity LDAP Server for details.Click Test to test the connection.
If the connection is established, then a Successfully Done message appears.
Feedback
Was this page helpful?