Insight Certificates
The default certificates provided are signed using the system-generated Protegrity-CA certificate. However, after installation custom certificates can be used. Ensure that all the certificates are signed by the same CA as shown in the following diagram.
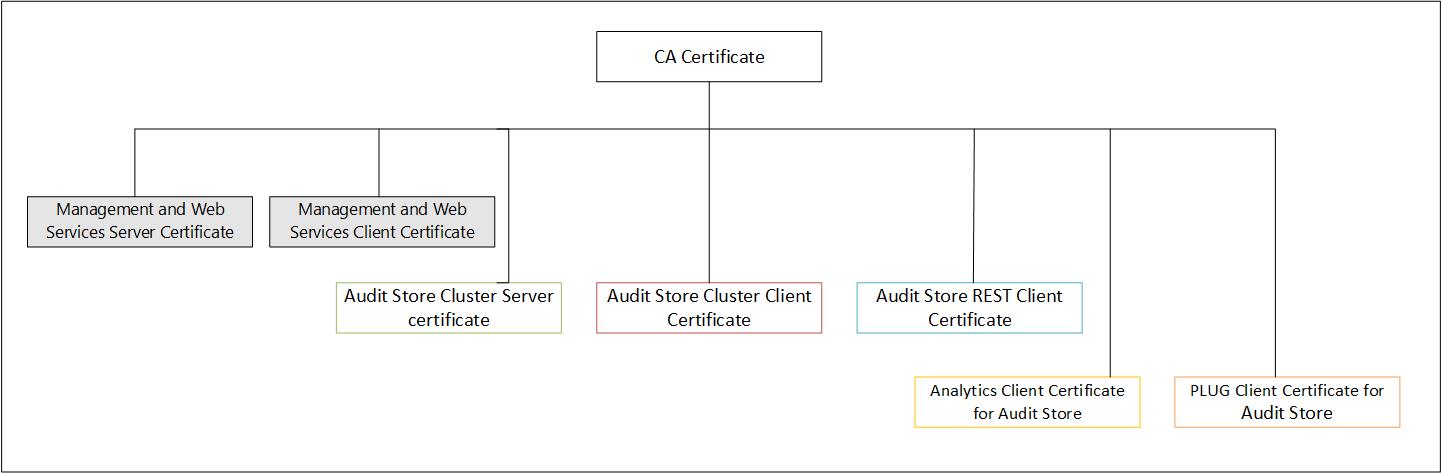
Update the certificates in the following order:
- Audit Store Cluster certificate
- Audit Store REST certificate
- PLUG client certificate for Audit Store
- Analytics client certificate for Audit Store
The various certificates used for communication between the nodes with their descriptions are provided here. The passphrase for the certificates are stored in the /etc/ksa/certs directory.
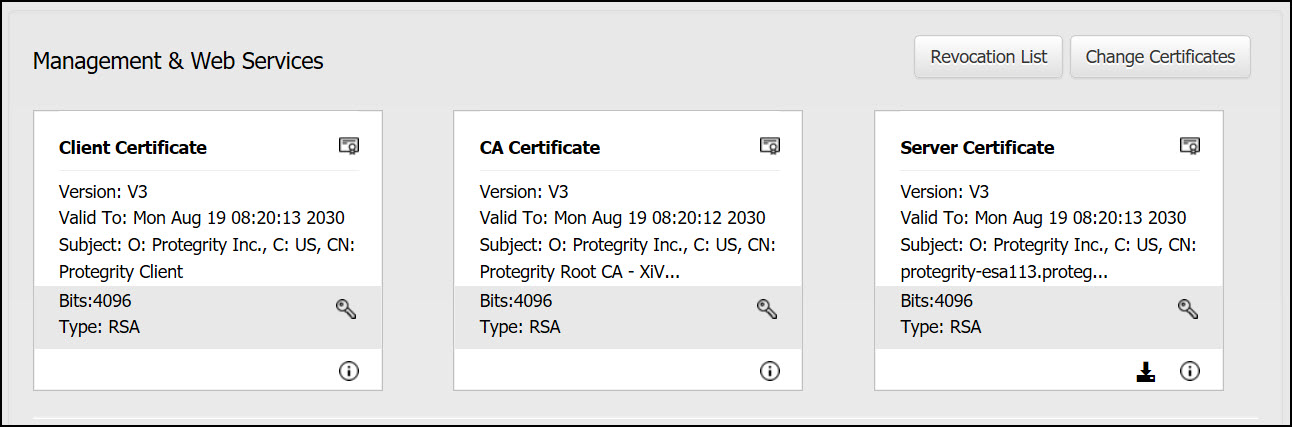
Management & Web Services: These services manages certificate-based communication and authentication between the ESA and its internal components and between ESA and external clients (REST).
For more information about Management and Web Services certificates, refer to Certificates in the ESA.
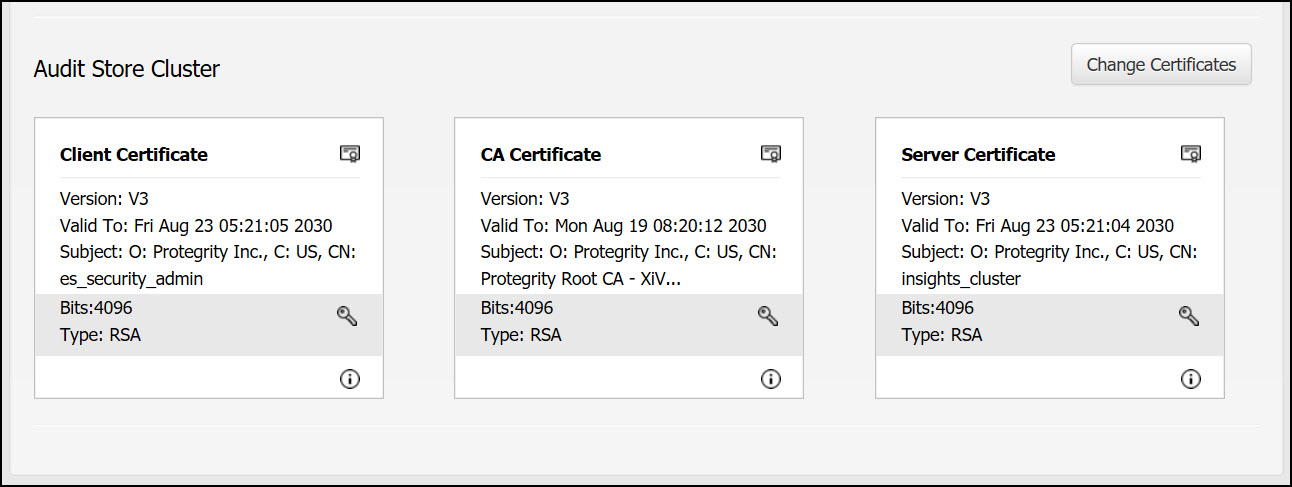
Audit Store Cluster: This is used for the Insight inter-node communication that takes place over the port 9300. These certificates are stored in the /esa/ksa/certificates/as_cluster directory on the ESA.
Server certificate: The server certificate is used for for inter-node communication. The nodes identify each other using this certificate. The Audit Store Cluster and Audit Store REST server certificate must be the same.
Client certificate: The client certificate is used for applying and maintaining security configurations for the Audit Store cluster.
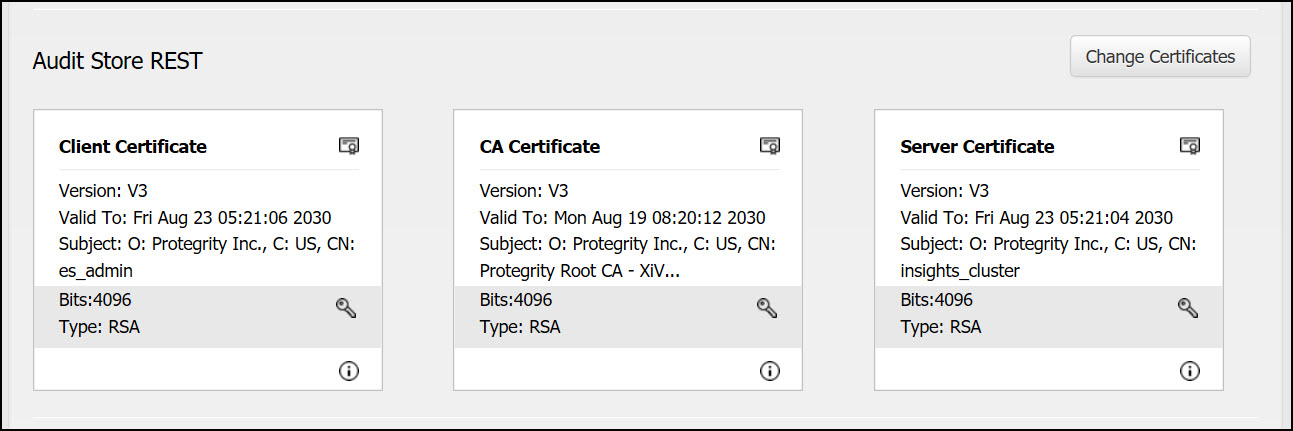
Audit Store REST: This is used for the Audit Store REST API communication over the port 9200. These certificates are stored in the /esa/ksa/certificates/as_rest directory on the ESA.
Server certificate: The server certificate is used for mutual authentication with the client. The Audit Store Cluster and Audit Store REST server certificate must be the same.
Client certificate:The client certificate is used by the Audit Store nodes to authenticate and communicate with the Audit Store.
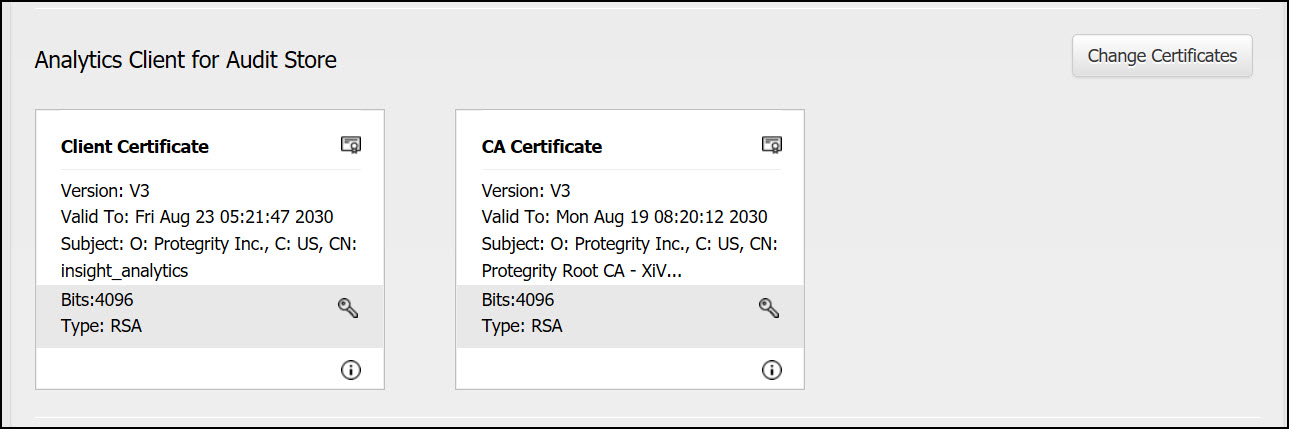
Analytics Client for Audit Store: This is used for communication between Analytics and the Audit Store. These certificates are stored in the /esa/ksa/certificates/ian directory on the ESA.
Client certificate: The client certificate is used by Analytics to authenticate and communicate with the Audit Store.
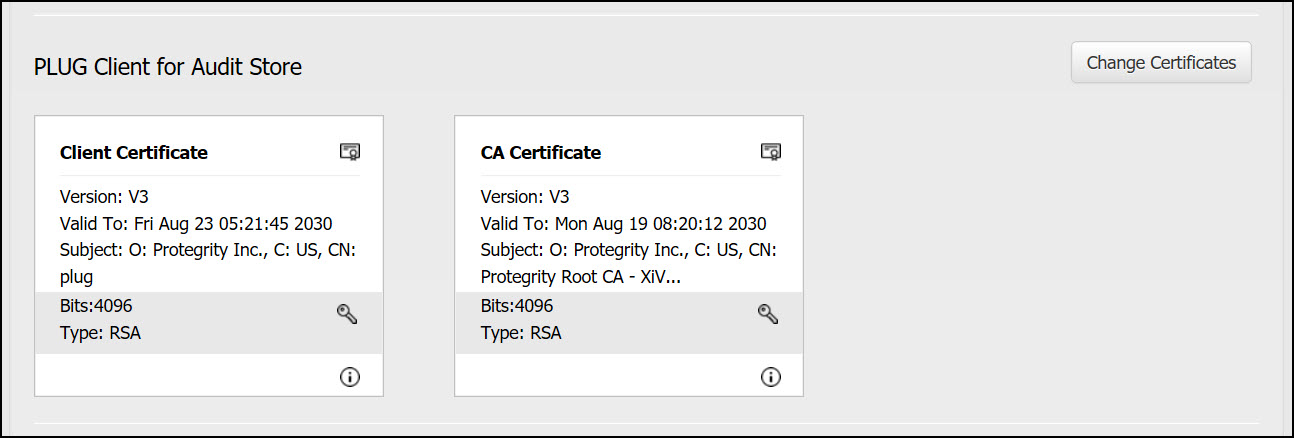
PLUG Client for Audit Store: This is used for communication between Insight and the Audit Store. These certificates are stored in the /esa/ksa/certificates/plug directory on the ESA.
Client certificate: The client certificate is used by the Log Forwarder to authenticate and communicate with the Audit Store.
Using custom certificates in Insight
The certificates used for Insight are system-generated Protegrity certificates. If required, upload and use custom CA, Server, and Client certificates for Insight.
For custom certificates, ensure that the following prerequisites are met:
Ensure that all certificates share a common CA.
Ensure that the following requirements are met when creating the certificates:
The CN attribute of the Audit Store Server certificate is set to insights_cluster.
The CN attribute of the Audit Store Cluster Client certificate is set to es_security_admin.
The CN attribute of the Audit Store REST Client certificate is set to es_admin.
The CN attribute of the PLUG client certificate for the Audit Store is set to plug.
The CN attribute of the Analytics client certificate for the Audit Store is set to insight_analytics.
The Audit Store Server certificates’ must contain the following in the Subject Alternative Name (SAN) field:
- Required: FQDN of all the Audit Store nodes in the cluster
- Optional: IP addresses of all the Audit Store nodes in the cluster
- Optional: Hostname of all the Audit Store nodes in the cluster
For a DNS server, include the hostname and FQDN details from the DNS sever in the certificate.
Ensure that the certificates are generated using a 4096 bit key.
For example, an SSL certificate with the SAN extension of servers ESA_Server_1, ESA_Server_2, and ESA_Server_3 in a cluster will have the following entries:
- ESA_Server_1
- ESA_Server_2
- ESA_Server_3
- ESA_Server_1.protegrity.com
- ESA_Server_2.protegrity.com
- ESA_Server_3.protegrity.com
- IP address of ESA_Server_1
- IP address of ESA_Server_2
- IP address of ESA_Server_3
When upgrading from an earlier version to ESA 8.1.0.0 and later with custom certificates, run the following step after the upgrade is complete and custom certificates are applied for Insight, that is, td-agent, Audit Store, and Analytics, if installed.
From the ESA Web UI, navigate to System > Services > Audit Store.
Ensure that the Audit Store Repository service is not running. If the service is running, then stop the service using the stop (
 ) icon in the Actions column.
) icon in the Actions column.Configure the custom certificates and upload it to the Certificate Repository.
Set the custom certificates for the logging components as Active.
From the ESA Web UI, navigate to System > Services > Audit Store.
Start the Audit Store Repository service using the start (
 ) icon in the Actions column.
) icon in the Actions column.In the ESA Web UI, click the Terminal Icon in lower-right corner to navigate to the ESA CLI Manager.
Navigate to Tools.
Run Apply Audit Store Security Configs.
Continue the installation to create an Audit Store cluster or join an existing Audit Store cluster.
For more information about creating the Audit Store cluster, refer here.
Feedback
Was this page helpful?