Validating Certificates
Verifying the validity of a certificate
You can verify a client or a server certificate using the following commands:
```
openssl verify -CAfile /etc/ksa/certificates/CA.pem /etc/ksa/certificates/client.pem
openssl verify -CAfile /etc/ksa/certificates/CA.pem /etc/ksa/certificates/ws/server.pem
```
If the client or server certificate is signed by the provided CA certificate, then the certificate is valid. The message **OK** appears.
Verifying the purpose of a certificate
You can verify if the certificate is a client, a server, or a CA certificate using the following command:
```
openssl x509 -in <Certificate name> -noout -purpose
```
For example, run the following command to verify the purpose of the client certificate:
```
openssl x509 -in /etc/ksa/certificates/client.pem -noout -purpose
```
Extracting the CN of a certificate
To extract the username of a certificate, you must pass the DN value to the pty_get_username_from_certificate function. The following steps explain how to extract the CN of a certificate.
In the CLI Manager, navigate to Administration > OS Console..
Run the following command to extract the value that is in the Subject attribute of the certificate.
openssl x509 -noout -subject -nameopt compat -in /etc/ksa/certificates/client.pemRun the following command to extract the username from the Subject attribute of the client certificate.
/etc/ksa/pty_get_username_from_certificate.py "<Value in the Subject attribute of the client certificate>"For example,
/etc/ksa/pty_get_username_from_certificate.py "/O=Acme Inc./C=US/CN=Protegrity Client"
The CN attribute in a certificate can contain the Fully Qualified Domain Name (FQDN) of the client or server. If the length of the FQDN is greater than 64 characters, the hostname is considered as CN to generate a certificate.
Working with intermediate CA certificates
A root certificate is a public key certificate that identifies the root CA. The chain of certificates that exist between the root certificate and the certificate issued to you are known as intermediate CA certificates. You can use an intermediate CA certificate to sign the client and server certificates.
If you have multiple intermediate CA certificates, then you must link all the intermediate certificates and the root CA certificates into a single chain before you upload to the Certificate repository.
The following figure illustrates an example of two intermediate certificates and a root certificate.
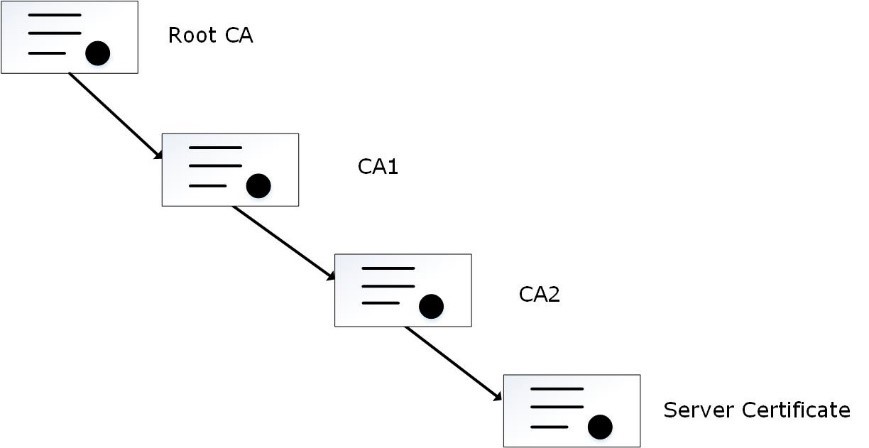
In the figure, the server certificate is signed by an intermediate certificate CA2. The intermediate certificate CA2 is signed by CA1, which is signed by the root CA.
You can merge the CA certificates using the following command in the OS Console:
cat ./CA2.pem ./CA1.pem ./rootCA.pem > ./newCA.pem
You must then upload the newCA.pem certificate to the Certificate Repository.
Ensure that you link the CA certificates in the appropriate hierarchy.
Increasing the Log Level to view errors for certificates:
If you want to view the errors and warnings generated for certificates, then you can increase the LogLevel attribute.
In the CLI Manager, navigate to Administration > OS Console.
View the apache.mng.conf file using a text editor.
/etc/ksa/service_dispatcher/servers/apache.mng.confUpdate the value of the LogLevel parameter from warn to debug and exit the editor.
View the apache.ws.conf file using a text editor.
/etc/ksa/service_dispatcher/servers/apache.ws.confUpdate the value of the LogLevel parameter from warn to debug.
Navigate to Administration > Services. The Service Management screen appears.
Restart the Service Dispatcher service.
Navigate to the /var/log/apache2-service_dispatcher directory.
Open the error.log file to view the required logs.
After debugging the errors, ensure that you revert the value of the LogLevel parameter to warn and restart the Service Dispatcher service.
Feedback
Was this page helpful?