Tokenization Portal
After you set up a cluster between the ESA and multiple DSG nodes, the policies are deployed on respective DSG nodes. Each policy has related data elements, data stores, and roles. You can use the Tokenization Portal menu to examine protection or unprotection of data when a protection data element is used.
The Tokenization Portal provides an interface where you can select the data security operation you want to perform, along with the DSG node, data elements available in the policies deployed at that node, and an external IV value. Every protection operation performed through the Tokenization Portal is recorded as an event in Forensics.
To access the test utilities, in the browser, enter (https://ESA_IP/3.3.0.0.5/1/TokenizationPortal).
Before you access the Tokenization Portal, ensure that the following pre-requisites are met:
- Ensure that any user who wants to access the test utilities must be granted the Cloud Gateway User and Policy User permissions.
- Ensure that the ESA where you are accessing Tokenization Portal is a part of the cluster.
- Ensure that the policy on the ESA is deployed to all the DSG nodes in the cluster.
- Ensure that the policy is synchronized across all the ESAs in the cluster.
The following image illustrates the UI options on the Tokenization Portal tab.
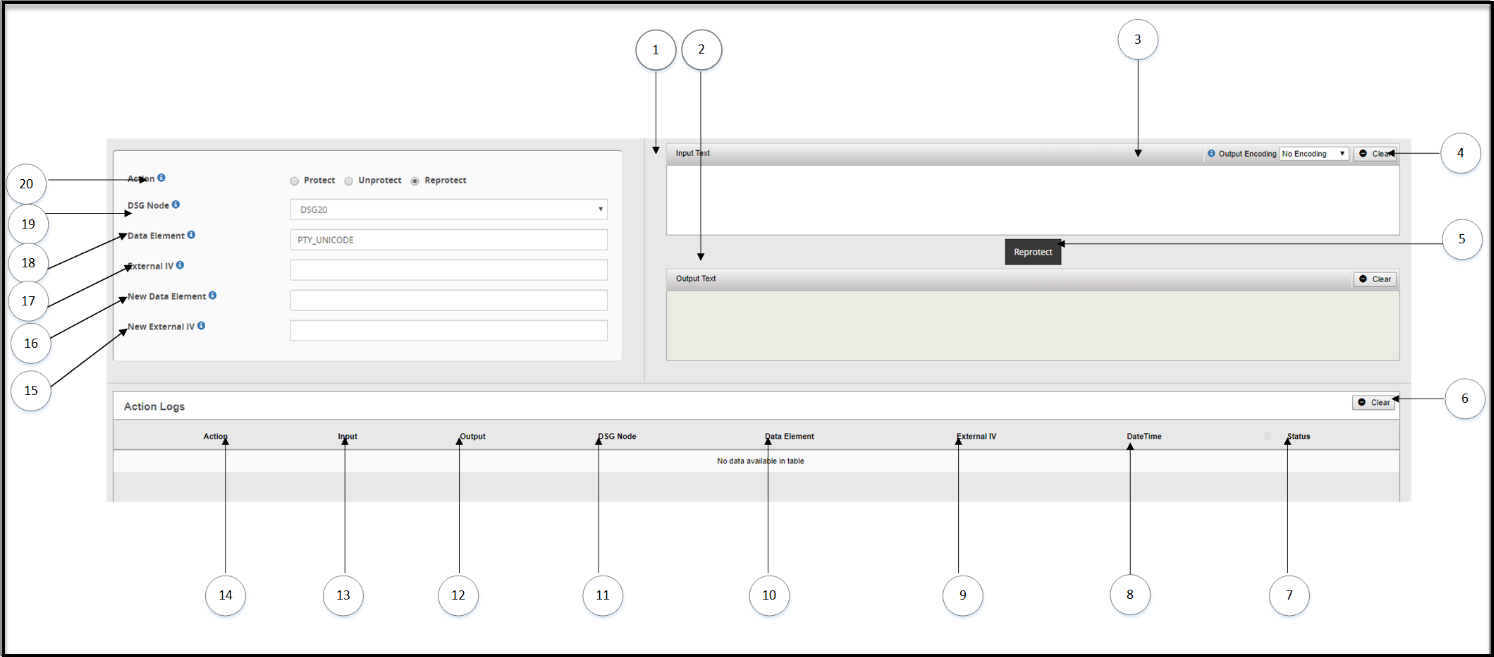
The following table provides the description for each of the available Tokenization tab options:
| Callout | Column/Textbox/Button | Sub-Columns | Description | Notes |
|---|---|---|---|---|
| 1 | Input Text | Enter the data you want to protect or unprotect. | ||
| 2 | Output Text | Transformed data, either protected or unprotected based on operation selected. | ||
| 3 | Output Encoding* | Select the type of encoding you want to use. Though the Output Encoding option is part of the Input Text area, remember that encoding is applied to Input data during protection and reprotection, and output data during unprotection. | ||
| 4 | Clear | Clear the text in the Input Text or Output Text box. | ||
| 5 | Unprotect/Protect/Reprotect | Click to perform security operation on the Input Text. You can either Protect, Unprotect, or Reprotect Data. | This option changes to Protect, Unprotect, or Reprotect based on the Action selected for data security operation. | |
| 6 | Clear | Clear the text in the Input Text or Output Text box. | ||
| Action Logs | Logs related to the data protection or unprotection are displayed under this area. These logs are cached in the browser session and are not persisted in the system. | |||
| 7 | Status | Displays | ||
| 8 | DateTime | Date and time when the data security operation was performed. | ||
| 9 | External IV | External IV value that was used for the data security operation. | ||
| 10 | Data Element | Data element used. | ||
| 11 | DSG Node | The DSG node where the data security operation was performed. | ||
| 12 | Output | Transformed data. | ||
| 13 | Input | Input data. | ||
| 14 | Action | Data security operation performed. | ||
| 15 | New External IV | New external IV value that will be used along with the protect or unprotect algorithm to create more secure encrypted data. | This field applies to the Reprotect option only. | |
| 16 | New Data Element | New data element that will be used to perform data security operation. | This field applies to Rthe eprotect option only. | |
| 17 | External IV | External IV value that will be used along with the protect or unprotect algorithm to create more secure encrypted data. | ||
| 18 | Data Element | Data element that will be used to perform data security operation. | ||
| 19 | DSG Node | The DSG node where the data security operation will be performed. | ||
| 20 | Action | Data security operation, Protect, Unprotect, or Reprotect that you want to perform. |
* - The available encoding options are as follows:
- Output Encoding: The field appears when action selected is either Protect or Reprotect.
- Input Encoding: The field appears when action selected is Unprotect.
Feedback
Was this page helpful?