Protegrity Gateway Product
The Protegrity Gateway Technology applies security operations on the network. The Data Security Gateway (DSG) offers flexibility and can run in the following environments:
- On-premise: Appliance runs on dedicated hardware.
- Virtualized: The appliance runs on a virtual machine.
- Cloud: The appliance runs on or is as part of a Cloud-based service.
SaaS based business applications are being adopted at a rapid pace. Organizations use SaaS-based application to fulfill different business needs. For example, SaaS based CRM applications can be used to manage their customer relationship. Company’s purchasing SaaS applications are outsourcing the burden of development, maintenance, and infrastructure to the SaaS vendors. A subscription contract and a browser are all that is required.
These SaaS applications store corporate data in the cloud and some of which may be sensitive. The DSG can be used to protect sensitive data as it moves from a corporate environment to the SaaS application storage on the cloud. When the data is returned, the sensitive protected data is unprotected and delivered to the intended user in a usable form.
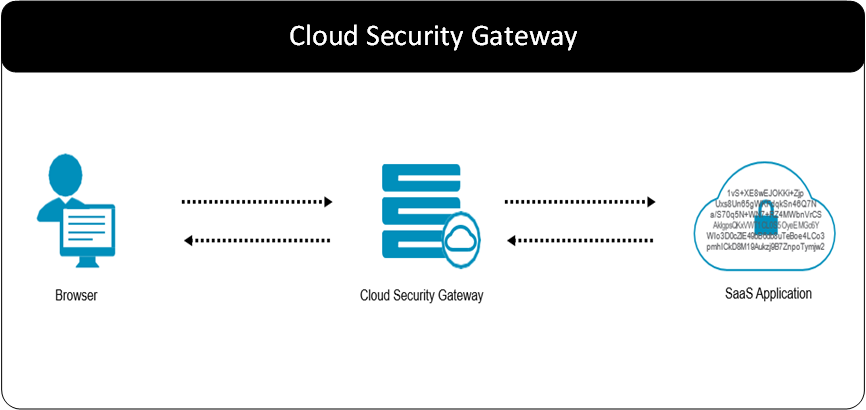
CoP Profiles are available for certain SaaS applications. Also, profiles can be created to configure the DSG to protect and unprotect sensitive data for a specific SaaS application. The DSG delivers differentiation from other vendors described in the following points:
Security: DSG protects sensitive data that is stored in the SaaS cloud storage. This data is rendered in an unusable form to system administrators who maintain the SaaS application. If security imposed by the SaaS application is breached, the data still stays protected. Cryptographic keys used to protect and unprotect sensitive data are stored in the premise. This gives control over the sensitive data.
This platform can be used for Data Residency Applications that have been recently highlighted by the changes in the European safe harbor requirements.
Enterprise data security: CoP profiles use the data security policy rules to control how sensitive data is protected throughout an organization. These rules are created in ESA by the security professionals. Data protected in the SaaS and that moves between business systems realize the benefit of a consistent enterprise data security model. Secured data is interoperable between business systems. Data is then secured at rest and in transit.
Agility: SaaS applications are built on a SaaS model. This model allows SaaS to add functionality with minimal effort of installing new software or other complexities. A new feature is developed and made available the next time a user loads the application on their browser. Thus, the applications are subject to change.
Data security solutions that protect SaaS applications must be agile in reacting to these changes. Certain SaaS data security vendors require building new products to accommodate these changes in their security solution. DSG uses the Configuration over Programming (CoP) to manage these changes. The CoP model uses profiles, that require no programming, to configure the changes.
SaaS change monitoring: Companies subscribe to SaaS applications as it readily lets them add business functionality to their business. These SaaS applications are subject to change. These changes should not break the security solution. Protegrity maintains systems that track these SaaS changes and test against the CoP Profiles that have been created for a specific SaaS. These changes will be identified and CoP Profile configuration modifications will be provided to secure and run a business.
Pricing model: The DSG can be purchased with the same model that is used to purchase the SaaS applications themselves. This makes the process of adding security to the SaaS applications as seamless as possible.
Third-party integration: Often, SaaS applications will communicate with other SaaS applications and business processes through RESTful APIs. DSG can be used to perform security operations between these systems. For example, data in a SaaS application like Salesforce may require protection. When data is pulled from Salesforce into other third party application, the data may be in the clear. DSG can intercept these APIs and unprotect data that needs to be used in the third-party business process.
The DSG applies data security operations on the network and uses the CoP Profiles to configure a data security solution.
When building modern business applications, browsers are the primary means of interaction between users and the business system. Network based protocols, such as web services or RESTful APIs, form the way of communicating with business functions or systems.
Flexibility: DSG can be applied to several use cases that are outside the realm of SaaS applications. This “Swiss Army Knife” type of product can single-handedly account for different data security scenarios. These scenarios together will constitute a holistic and complete solution. This is a powerful addition to the development set of tools.
Transparency: Today, most data security solutions require integration with the host business system components. These components include business applications and databases. By applying security operations on the network, DSG reduces the amount of work required to protect the organization.
Enterprise: Data protection with DSG can be combined with any other protector in the Protegrity Data-Centric Audit and Protection platform. If the gateway does not meet a specific requirement, data security solution can be fulfilled with other protectors in the platform.
The set of security scenarios described in the following section gives a glimpse of the flexibility of this product.
DSG used to protect web applications
Most applications today are based on a web interface. Web interfaces have an architecture that protect data from the browser to the Web Server with HTTPS. The Web Server terminates HTTPS and the traffic flows through Application Servers. Finally, the traffic flows into a data store. Sometimes there are business systems that process data from the databases.
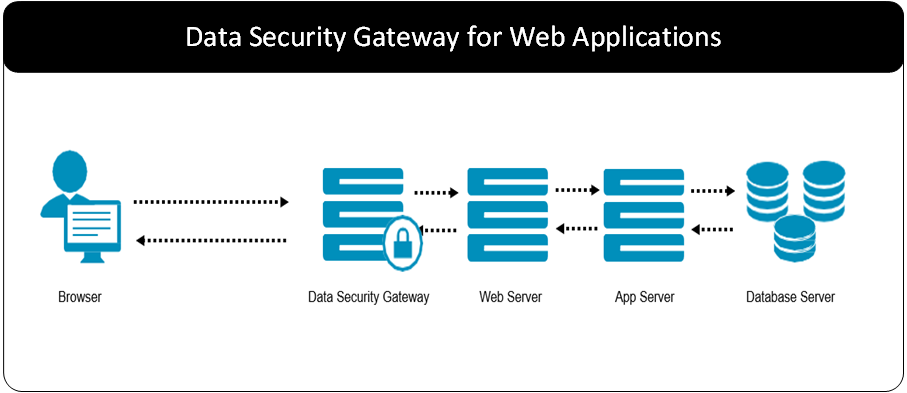
From a security point of view, the data that is flowing after HTTPS is terminated will be in the clear. Adding a DSG before the Web Server can terminate HTTPS and execute the CoP Profile to extract and protect any sensitive data. For example, if an SSN is entered in a web form, a specific CoP Profile rule can be created. This rule picks out the HTML label associated with the value entered and protects the SSN.
Like Web Servers and App Servers, the DSGs are stateless and can be placed behind a load balancer. Vertical and horizontal scaling can manage the throughput required to maintain business performance.
Consider the following cases:
- Business functions are performed in the App Server on sensitive data.
- Business functions are performed in the database itself within stored procedures.
In such cases, DSG provides a RESTful API Server. Database UDFs from Protegrity Database Protector can also be used.
Data security gateway as an API security gateway
APIs are the interoperability language of modern architectures. Classic use of APIs is for interfaces internal to applications. Also, APIs are moving data and executing processes between disparity applications.
![DSG as an API gateway] DSG as an API gateway](/10.1/docs/images/dsg_fig8.png)
These APIs are implemented in the form of SOAP based Web Services or RESTful APIs. In these scenarios, techniques to implement both the client and the server component can be used. The server component may also come from different vendors.
Irrespective of how this architecture is implemented, the DSG can be placed between the client and the server. Here, a CoP Profile can be used to specify what and how sensitive data passing in either direction will be protected or un-protected.
DSG for files
A common scenario found in enterprises today is the delivery of files into an organization from business partners. Often, the security approach to protecting data in transit from the source to the destination is SFTP.
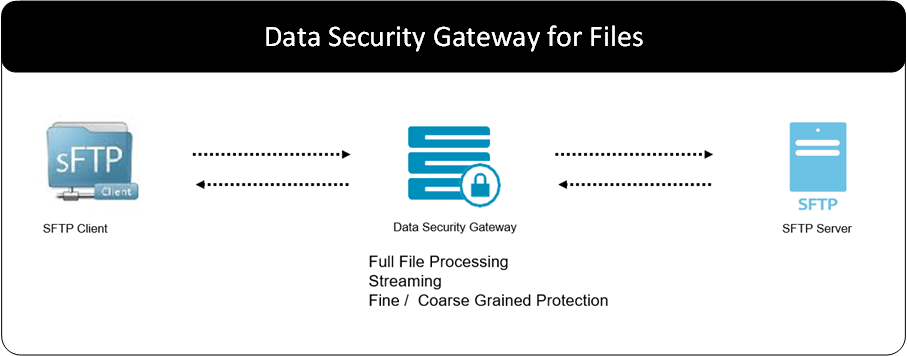
However, when the file lands in the SFTP Server, the encryption is terminated and the sensitive fields in the clear. This is similar to the web application scenario for the HTTPS server. The data downstream is exposed in the clear.
The DSG can be placed before the file lands on the SFTP Server. It can terminate the security making the payload visible to the gateway. A CoP Profile can be created to perform diverse types of security operations to the file.
Coarse Grained Protection: CoP Profile rules can be created to encrypt the entire file before it lands on the SFTP Server.
Fine Grained Protection: CoP Profile rules can be created to encrypt or tokenize specific data elements contained within the file.
DSG as an on-demand RESTful API server
RESTful APIs can be used to perform certain functions that are delivered by the REST Server. In context to data security, business applications can make requests to the DSG as a RESTful Server for data protection.

Protecting or unprotecting data is easy. Send the XML or JSON document that contains the data to be acted on and the CoP Profile rules take care of the rest. The rule will identify the exact part of the document and act on that data. There is no need to parse that data out and then reconstruct the document after the security operation is performed.
Feedback
Was this page helpful?