Log
Create a rule in the child node of the extract rule defined for the payload. The payload can be defined for services, such as, HTTP, SFTP, REST, and so on. When the extract rule is invoked for the payload, the log rule will display the contents of the payload in the gateway log.
The fields for the Logs action type are as seen in the following figure.
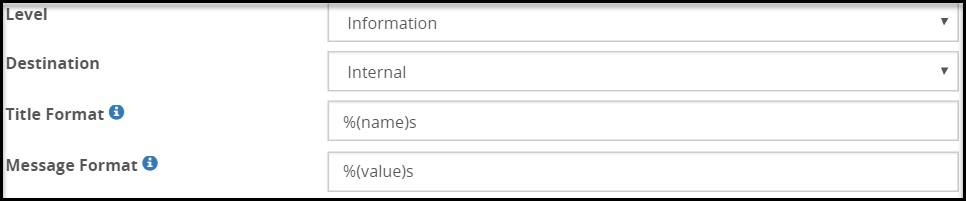
The properties for the Log action are explained in the following table.
| Properties | Description |
|---|---|
| Level* | Type of log to be generated. The type of log selected in this field decides the log entry that is displayed on the Audit screen in Forensics. |
| Destination** | Location where the log file is sent to is specified in this field. |
| Title Format | Used to format log message title using rule %(name) as a variable. Only applicable to destinations that support title. |
| Message Format | Used to format log message using %(value) as a variable. Value represent the data extracted by parent rule. |
* -In the Log action, depending on the severity of the message, you can define different types of log levels. The following table shows the DSG log level setting and the corresponding log entry that is seen in Forensics.
| DSG Log Level | Logging in Forensics |
|---|---|
| Warning | Normal |
| Error | High |
| Verbose | Lowest |
| Information | Low |
| Debug | Debug |
** The following options are available for the Destination field:
- Forensics: Log is sent to the Forensics and the DSG internal log.
- Internal: Log is sent only to the DSG internal log.
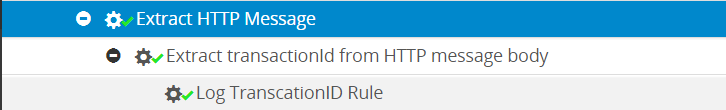
Consider the following example to understand the functionality of the Log action type. In this example, the Log action type functionality is used to find the transactionID from a sample text message in the HTTP payload. The following RuleSet structure is created to find the transactionID:
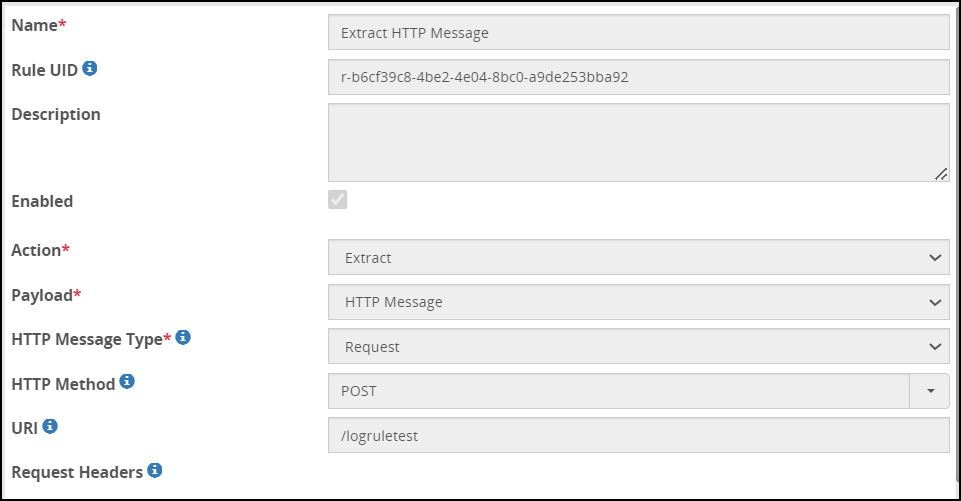
Create an extract rule for the HTTP payload using the default RuleSet template defined under the REST API service. The HTTP payload consists of the following sample text message:
{"source":{"merchantId":"LCPLC-lphf21","storeId":"LPHF2100303086", "terminalId":"0","operatorId":"10","terminalType":"GASPRO", "offline":false}, "message":{"transactionType":"WALLET","messageType":"VERIFYPARTNER", "transactionTime":"2018-05-09T11:48:47+0000", "transactionId":"20180509114847LPHF2100301237000090"}, "identity":{"key":"4169671111","entryType":"KEYEDOPERATOR"}}The fields for the extract rule for the HTTP message payload are as seen in the following figure:
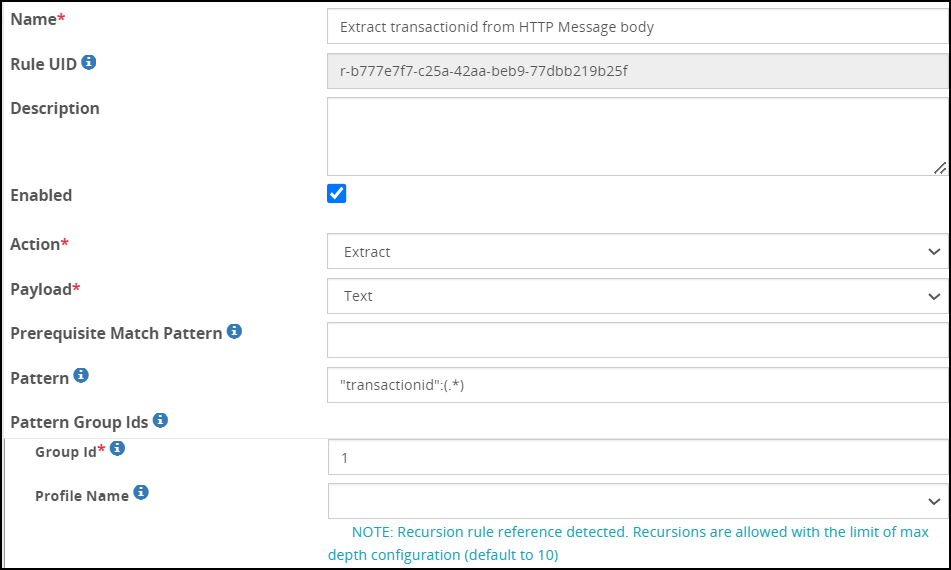
Create a child extract rule to extract the text message in the payload.
Create a RegEx expression, “transactionID”:(.*)", to match the pattern for the transactionID. The fields for the child extract rule are as seen in the following figure:
Create another child rule for the Log action type. The fields for the Log action type are as seen in the following figure:
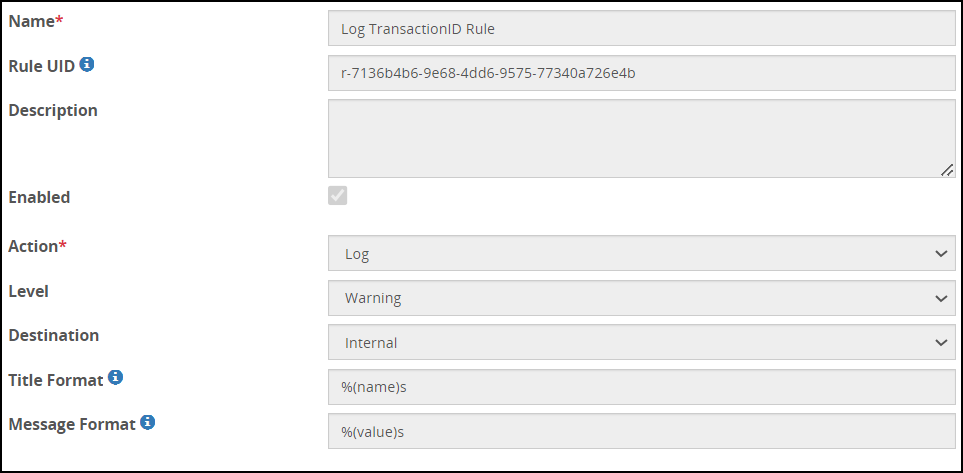
Add the following values in the Log action type.
- Action: Log
- Level: Warning
- Destination: Internal
- Title Format: %(name)s
- Message Format: %(value)s
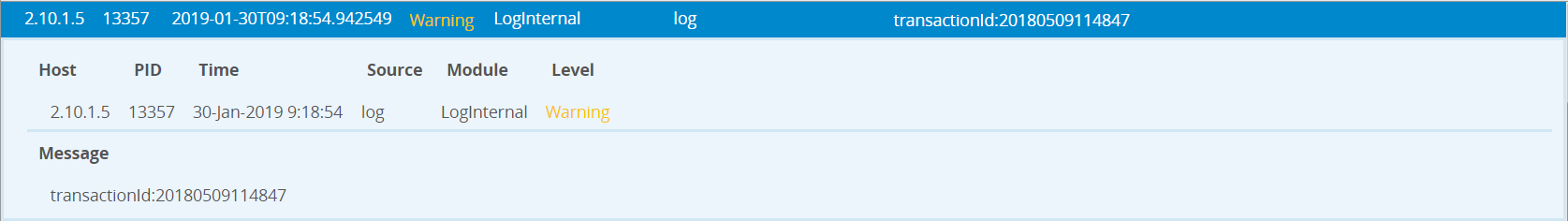
After the log rule is processed, the following message will be displayed in the DSG internal log:
Feedback
Was this page helpful?