Set Context Variable
You can The value set due to this rule will be maintained throughout the rule lifecycle.
The following table describes the Variable Name type supported by the Set Context Variable option.
| Field | Description |
|---|---|
| User IP Addr | Captures the client IP address forwarded by the load balancer that distributes client requests among DSG nodes. This IP address is displayed in the audit log. |
| Value-External IV Protect, Unprotect | Uses the External IV value that is sent in the header to protect or unprotect data. This value overrides the value set in the Default External IV field in the Transform rule. |
| Value-External IV Reprotect | Uses the External IV value that is sent in the header to reprotect data. This value overrides the value set in the Reprotect External IV field in the Transform rule. |
| Dynamic Rule | Used when Dynamic CoP is implemented for the given Ruleset hierarchy. A request header with Dynamic CoP rule accesses the URI to complete the Ruleset execution. |
| Client Correlation Handle | Captures the Linux epoch time when the protect or unprotect operation is successful. |
| User Defined Headers | Extracts JSON data from the input and set it into the response header. The JSON data is extracted into key-value pairs and appended in the response header. This field also accepts list of lists as input. For example, [["access-id","asds62231231"],["secret-access-token","sdas1353412"]].Consider an example where in some sample JSON data, {"access-id":"asds62231231, "secret-access-token":"sdas1353412"}, is sent from a server to the DSG. After the DSG processes the request, the JSON data is extracted into key-value pairs and appended in the response header. The key will be the header name and the value will be the corresponding header value. The following snippet is displayed in the response header:access-id -> asds62231231secret-access-token -> sdas1353412 |
The Set Context Variable action type must always be created as a leaf node - a rule without any child nodes.
User IP address
Record the IP of the client that sents a request to a DSG node in the audit log. When a client request is sent to the load balancer that distributes incoming requests to the cluster of DSG nodes, the load balancer appends a header to the request. This header captures the client IP address.
The types of headers can be X-Forwarded-For, which is most commonly used, or X-Client-IP, User-Agent, and so on.
Before a Set Context Variable with the User IP Addr Variable Name type rule is created, an extract rule that extracts the Header with the given header name, such as X-Forwarded-For, from a request would be created.
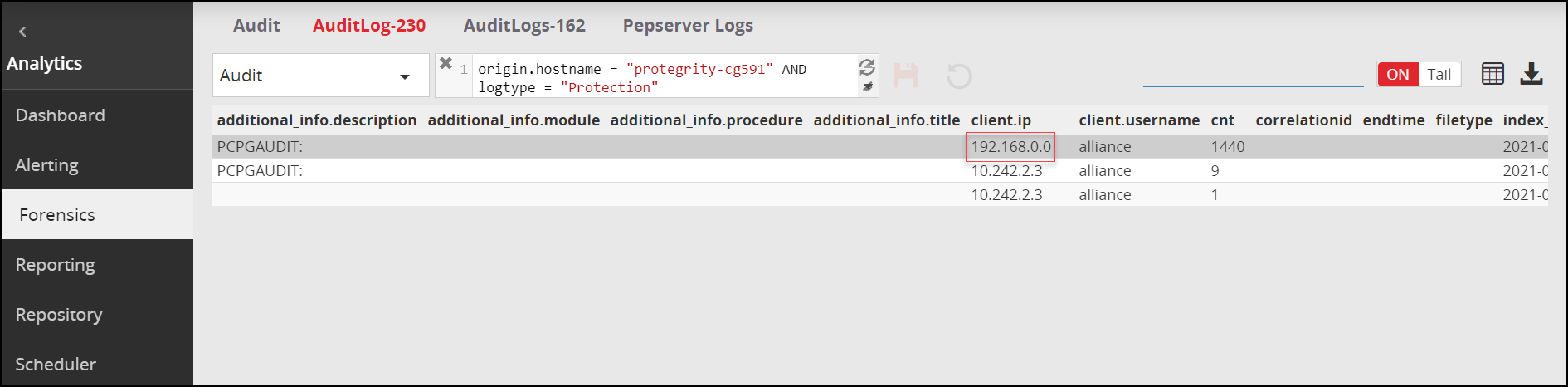
If a request header sends an IP address 192.168.0.0 as the X-Forwarded-For value, the following image shows the client IP in the Forensics log displaying this IP address value.
The fields for the Variable Name type are as seen in the following figure.
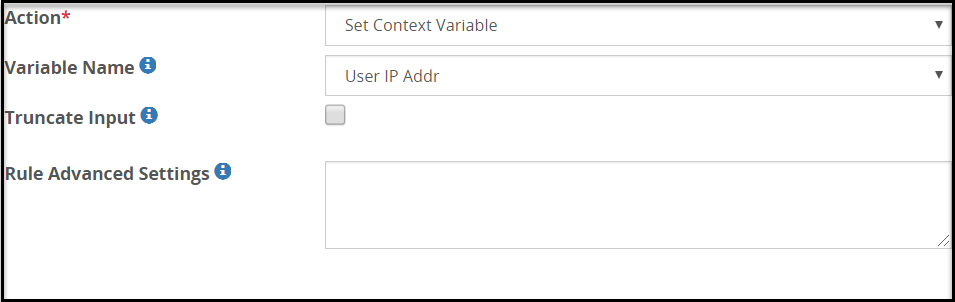
The following table describes the fields.
| Field | Description | Default (if any) |
|---|---|---|
| Truncate Input | Select this check box to truncate any context variable value passed in the header that exceeds the maximumInputLength set in the Rule Advanced Settings.If this check box is not selected and the value set in the context variable exceeds the length set in the maximumInputLength parameter, then the transaction fails with an error. | |
| Rule Advanced Settings | Set the parameter maximumInputLength such that data beyond this length is not set as the context variable. The datatype for this option is bytes. | 512 |
Value External IV protect
You can send an external IV value that will used along with the protect or unprotect algorithm in the request header to create more secure encrypted data. External IV values add additional layer of randomness and help in creating secure tokens.
Note: This value overrides the value set in the Default External IV field in the Transform rule.
The fields for the Variable Name type are as seen in the following figure.
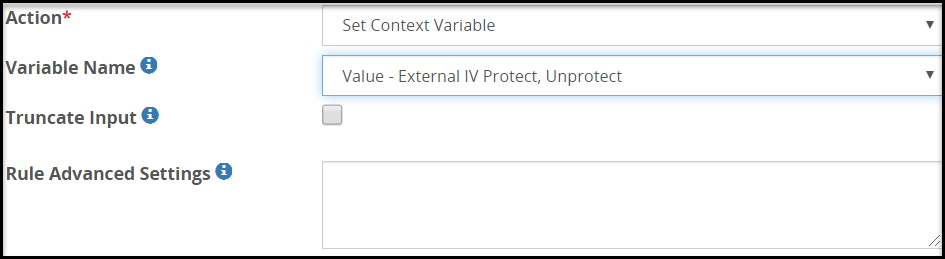
The following table describes the fields.
| Field | Description | Default (if any) |
|---|---|---|
| Truncate Input | Select this check box to truncate any context variable value passed in the header that exceeds the maximumInputLength set in the Rule Advanced Settings.If this check box is not selected and the value set in the context variable exceeds the length set in the maximumInputLength parameter, then the transaction fails with an error. | |
| Rule Advanced Settings | Set the parameter maximumInputLength such that data beyond this length is not set as the context variable.The datatype for this option is bytes. | 512 |
Note: If an External IV value is sent in the header to protect or unprotect sensitive data, with the case-preserving and position-preserving property enabled in the Alpha-Numeric (0-9, a-z, A-Z) token type, then the External IV property is not supported.
Value-External IV Reprotect
You can send an external IV value that will used along with the reprotect algorithm in the request header to create more secure encrypted data. External IV values add additional layer of randomness and help in creating secure tokens.
Note: This value overrides the value set in the Default External IV field in the Transform rule.
The fields for the Variable Name type are as seen in the following figure.
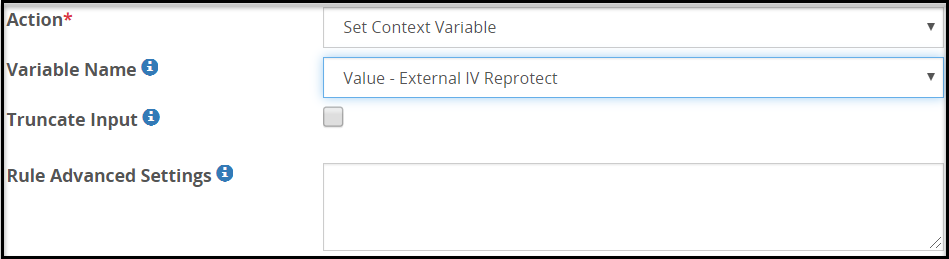
The following table describes the fields.
| Field | Description | Default (if any) |
|---|---|---|
| Truncate Input | Select this check box to truncate any context variable value passed in the header that exceeds the maximumInputLength set in the Rule Advanced Settings.If this check box is not selected and the value set in the context variable exceeds the length set in the maximumInputLength parameter, then the transaction fails with an error. | |
| Rule Advanced Settings | Set the parameter maximumInputLength such that data beyond this length is not set as the context variable.The datatype for this option is bytes. | 512 |
Note: If an External IV value is sent in the header to protect or unprotect sensitive data, with the case-preserving and position-preserving property enabled in the Alpha-Numeric (0-9, a-z, A-Z) token type, then the External IV property is not supported.
Dynamic Rule
The Dynamic Rule provides a hook in form of the URI in the preceding rule and a logical endpoint for the Dynamic CoP header request to join the rule tree.
After you define the Dynamic Rule variable name type, you can proceed with creating the Dynamic Injection action type.
The fields for the Variable Name type are as seen in the following figure.
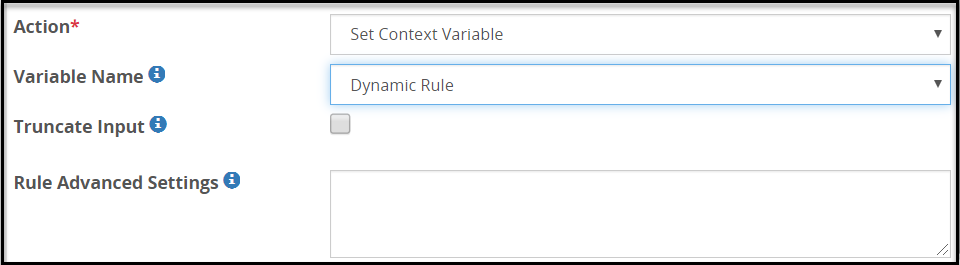
The following table describes the fields.
| Field | Description | Default (if any) |
|---|---|---|
| Truncate Input | Select this check box to truncate any context variable value passed in the header that exceeds the maximumInputLength set in the Rule Advanced Settings.If this check box is not selected and the value set in the context variable exceeds the length set in the maximumInputLength parameter, then the transaction fails with an error. | |
| Rule Advanced Settings | Set the parameter maximumInputLength such that data beyond this length is not set as the context variable.The datatype for this option is bytes. | 4096 |
Client Correlation Handle
The client correlation handle captures the Linux epoch time when the protect or unprotect operation is successful.
When you define rulesets, the rules are structured such that the extract rule identifies the protect successful event from the input message. This rule is followed by the extraction of the timestamp using a UDF rule.
The set context variable rule follows next to set the variable to the extracted timestamp. You can further create a rule that converts this timestamp to a hex value followed by a Log rule to display the exact time of protect and unprotect operation in the ESA Forensics or DSG logs.
The fields for the Variable Name type are as seen in the following figure.
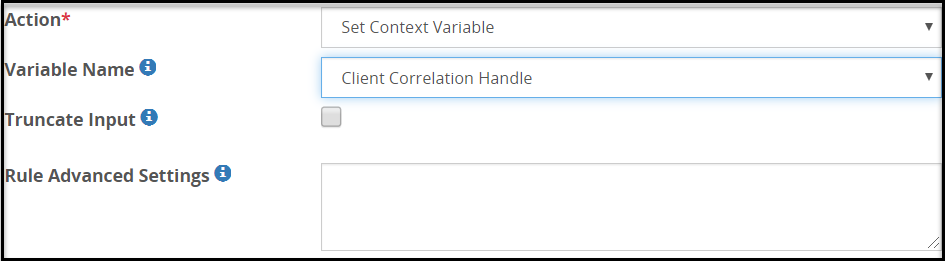
The following table describes the fields.
| Field | Description | Default (if any) |
|---|---|---|
| Truncate Input | Select this check box to truncate any context variable value passed to the Set Context Variable rule that exceeds the maximumInputLength parameter value set in the Rule Advanced Settings.Note: The maximum value that can be set for the maximumInputLength parameter value is 20. If this parameter is set to a value greater than 20, then the following warning message appears in the gateway startup logs and the context variable value is truncated to 20 characters. |
"Value configured by user is ignored as it exceeds
20 Characters (Maximum Limit)"
If this parameter is not configured, the context variable value is truncated to 20 characters by default.
If this check box is not selected and the context variable value passed to the Set Context Variable rule exceeds the maximumInputLength parameter value set in the Rule Advanced Settings, then the transaction fails with an error.| |
|Rule Advanced Settings|Set the parameter maximumInputLength such that data beyond this length is not set as the context variable. The datatype for this option is number of characters.|20|
User Defined Headers
User Defined Headers are meant to provide additional information about an HTTP Response Header that can be helpful for troubleshooting purposes. The User Defined Headers can include information such as custom cookies, state information, and provide information to the load balancer, for example, CPU utilization of a particular node behind the load balancer.
The fields for the Variable Name type are as seen in the following figure.
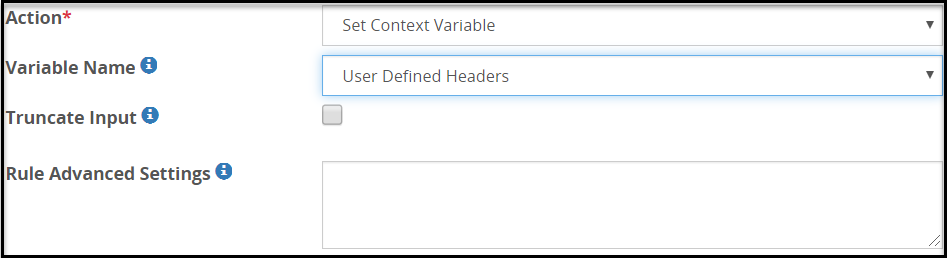
The following table describes the fields.
| Field | Description | Default (if any) |
|---|---|---|
| Truncate Input | Select this check box to truncate any context variable value passed in the header that exceeds the maximumInputLength set in the Rule Advanced Settings.If this check box is not selected and the value set in the context variable exceeds the length set in the maximumInputLength parameter, then the transaction fails with an error. | |
| Rule Advanced Settings | Set the parameter maximumInputLength such that data beyond this length is not set as the context variable.The datatype for this option is bytes. | 4096 |
Feedback
Was this page helpful?