Security Assertion Markup Language (SAML) codec
Any SAML implementation involves the following two entities, namely, the Single Sign-On (SSO) application or the Service Provider that the user is trying to access and the Identity Provider (IDP) responsible for authenticating the user.
A typical SAML implementation is illustrated in the following diagram.
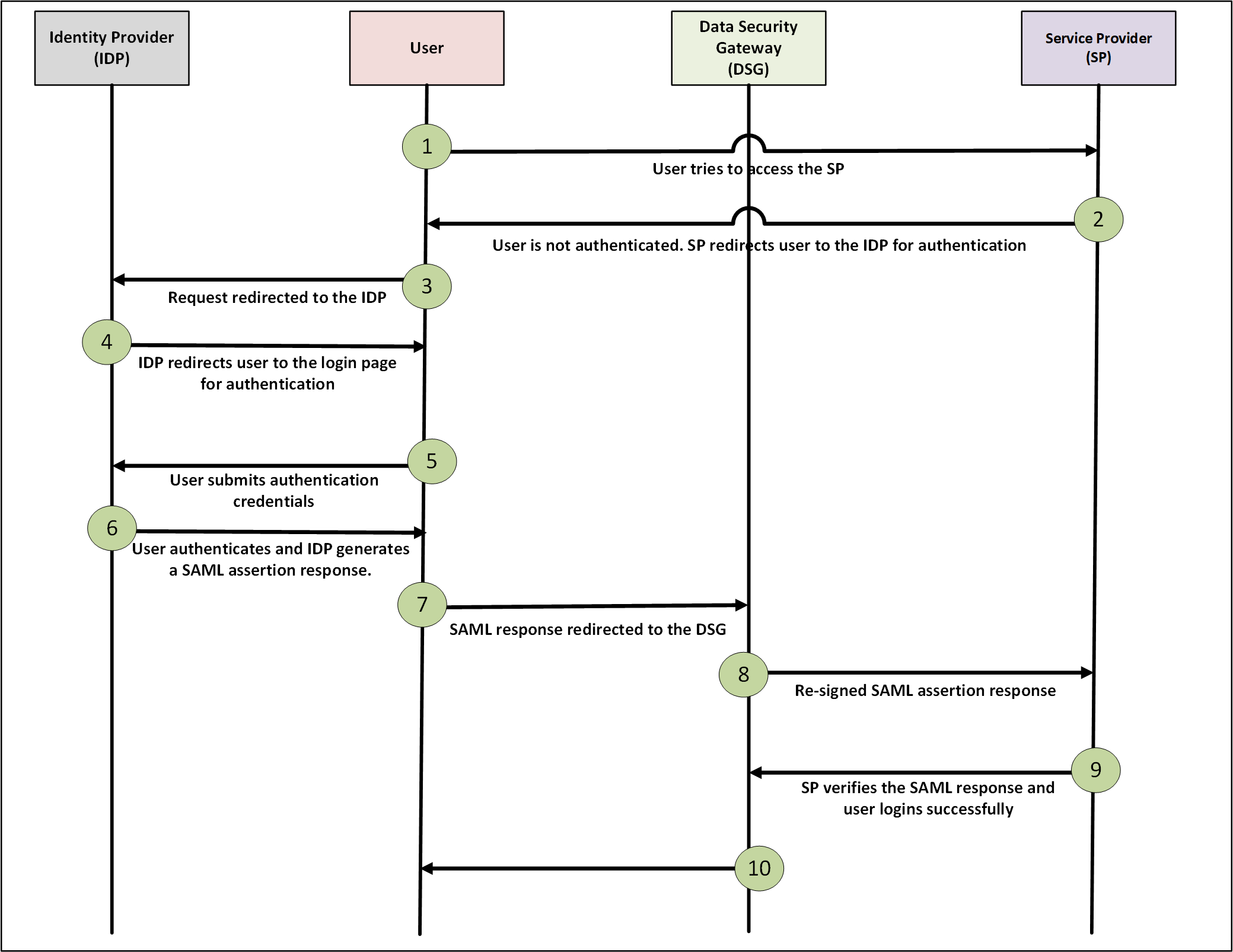
Consider that the user wants to access the Service Provider (SP). The SP redirects the user’s authentication request to the Identity Provider (IDP) through the DSG.
When a user tries to access a Service Provider (SP), an authentication request is generated. The DSG receives and forwards the request to the IDP. The IDP authenticates the user and reverts with a SAML assertion response. The DSG updates the domain names in the SAML assertion response, verifies the inbound SAML signature, and re-signs the modified SAML response to ensure that the response is secure and not tampered. The response is then forwarded to the SP. The SP verifies the response and authenticates the user.
After this authentication is complete, when the same user tries to access any other SP on the same network, authentication is no longer required. The IDP identifies the user from the previous active session and reverts with a SAML response that user is already authenticated.
Note: SAML codec is tested with the following the SalesForce SP and the Microsoft Azure AD IDP.
Before you begin:
Ensure that the following prerequisites are met:
- The IDP’s public certificate, which was used to sign the message response, is uploaded to the ESA using the Certificate screen.
- The certificate and private key that the customer wants to use to re-sign the SAML response using the DSG must be uploaded to the ESA.
- The certificate that is used to re-sign the message must be uploaded to the SP for validating the response.
- As the user requests to access the SP are redirected to the IDP through the DSG, ensure that in the SP configurations, the IDP redirect URLs are configured.
For example, if the IDP is https:\\login.abc.com, then in the SP configurations ensure that the redirect URLs are set to https:\\secure.login.abc.com.
As the SAML response from the IDP, that is used to authenticate the user, is redirected through the DSG to the SP, ensure that the IDP configurations are set as required.
For example, if the SP is https:\\biloxi.com, then in the IDP configurations, ensure that the redirect URLs are set to https:\\secure.biloxi.com.
Note: After you upload the certificates to the ESA, ensure that you deploy configurations from the ESA such that the certificates and keys are pushed to all the DSG nodes in the cluster.
The SAML codec fields can be seen in the following image.
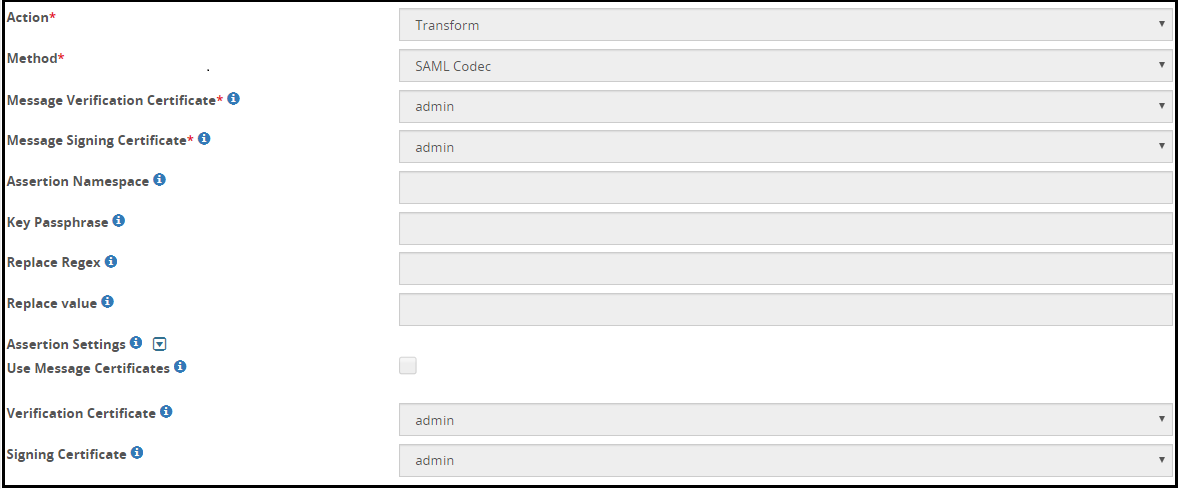
The following table describes the fields for the SAML codec.
| Field | Sub-Field | Description | Notes |
|---|---|---|---|
| Message Verification Certificate | Select the IDP’s public certificate from the list of available certificates drop down. | Ensure that the certificates are uploaded to the ESA from the Certificate screen. | |
| Message Signing Certificate | Select the certificate that will be used to re-sign the response from the list of available certificates drop down list. Both message and assertion signing is supported. | Ensure that the certificates are uploaded to the ESA from the Certificate screen. | |
| Assertion Namespace | Assertion namespace value defined in the SAML response. | This field is redundant. Any value that you enter in this field, will be bypassed. | |
| Key Passphrase | The passphrase for the encrypted signing key that will be used to re-sign the certificate. | This field is redundant. Any value that you enter in this field, will be bypassed. | |
| Replace Regex | Regex pattern to identify the forwarded hostname received from the IDP. You can also provide the exact hostname. | ||
| Replace value | Hostname that will be used to forward the SAML response. | ||
| Assertion settings | Use Message Certificates | Select this checkbox to use the same certificates that were used for verification of the SAML response to re-sign the assertions. | This field is redundant. Any value that you enter in this field, will be bypassed. |
| Verification Certificate | If you choose to use a certificate other than the one used to re-sign the message response, then select a certificate from the list of available certificates drop down list. | This field is redundant. Any value that you enter in this field, will be bypassed. | |
| Signing Certificate | If you choose to use a certificate other than the one used to re-sign the message response, then select a certificate from the list of available certificates drop down list. | This field is redundant. Any value that you enter in this field, will be bypassed. |
Feedback
Was this page helpful?