Protegrity Key Management
The following keys are a part of the Protegrity Key Management solution:
- Key Encryption Key (KEK): The cryptographic key used to protect other keys. It is also known as the Master Key (MK). It protects the Data Store Keys, Repository Keys, Signing Keys, and Data Element Keys.
- Data Encryption Key (DEK): The cryptographic keys used to protect sensitive data. The Data Encryption Keys (DEKs) are categorized as follows:
- Repository Key: It protects the policy information in the ESA.
- Signing Key: The protector utilizes the signing key to sign the audit logs for each data protection operation.
- Data Store Key: These keys are no longer used and are only present due to backward compatibility.
- Data Element Key: The cryptographic key that is used to protect sensitive data linked to an encryption data element.
Key Encryption Key (KEK) in Protegrity
- The Protegrity Key Encryption Key (KEK) is known as the Master Key (MK).
- It uses AES with a 256-bit key.
- The MK is non-exportable and is generated and stored within the active Key Store.
- The MK is responsible for protecting all the DEKs.
- The MK, RK, and signing key are generated when the ESA Policy and Key Management is initialized.
Data Encryption Keys (DEKs) in Protegrity
- The Repository Key (RK), Signing Key, Data Store Keys (DSKs), and Data Element Keys are collectively referred to as the (DEKs).
- The RK, Signing Key, and DSK are AES 256-bit keys.
- The Data Element Keys can be both 128-bit and 256-bit keys depending on the protection method used.
- The DEKs are generated by the active Key Store.
Key Usage Overview
In the Protegrity Data Security Platform, endpoint protection is implemented through policies. The keys form a part of the underlying infrastructure of a policy and are not explicitly visible.
The following figure provides an overview of the key management workflow.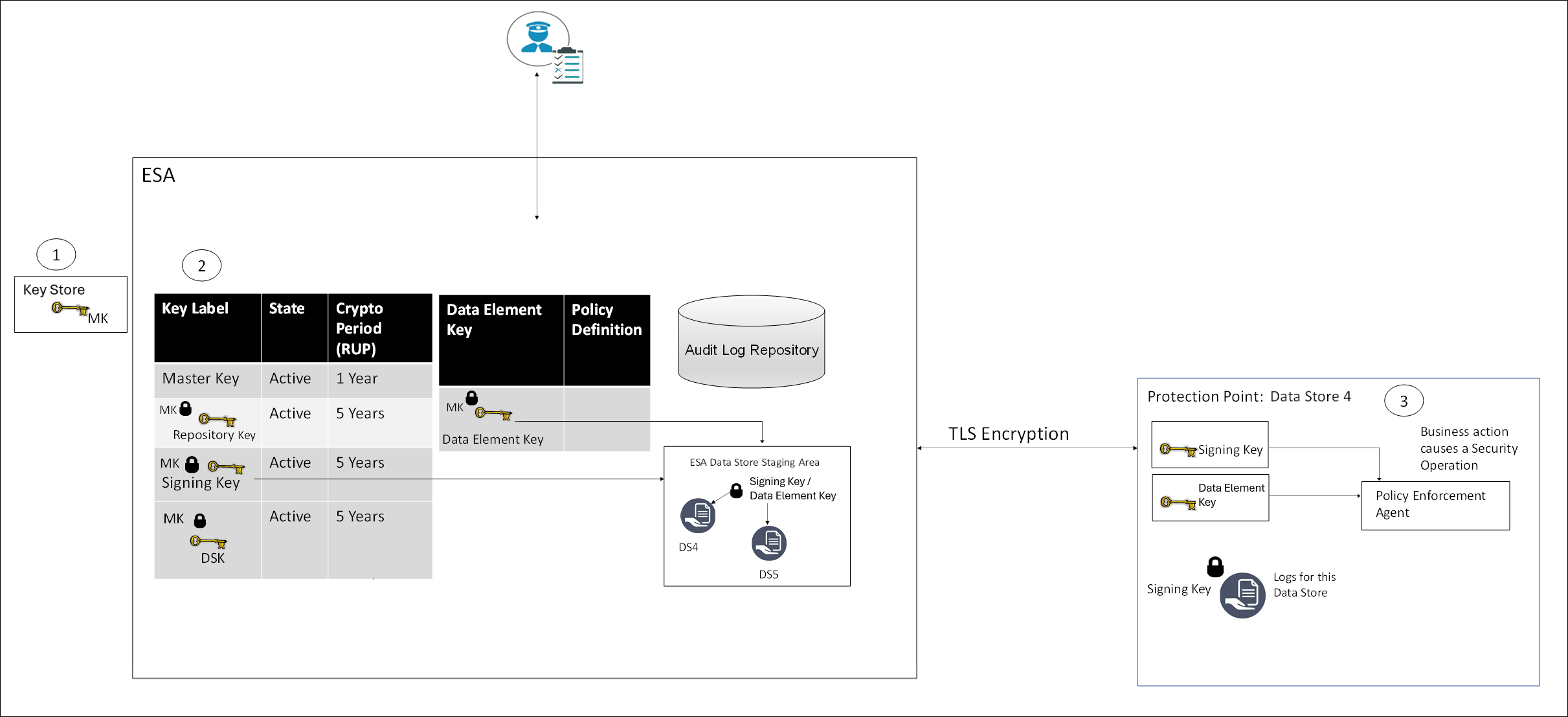
- All MKs are stored in the Key Store.
- In the ESA, all DEKs are stored and protected by the MK.
- In the Protector, the Signing key and Data Element Keys are stored in the memory.
Certificates
Certificates in Protegrity are generated when the ESA is installed. These certificates are used for internal communication between various components in the ESA. Their related keys are used for communication between the ESA and protectors.
For more information about certificates, refer to the section Certificates in ESA in the Certificate Management.
Key Store
A Key Store is a device used to generate keys, store keys, and perform cryptographic operations. The MK is stored in the Key Store and it is used to protect and un-protect DEKs.
When an enterprise implements a data protection solution in their infrastructure, they must carefully consider the type of Key Store to use as part of the implementation strategy. The Key Store can be connected to the Soft HSM, HSM, or KMS.
When the ESA is installed, the internal Protegrity Soft HSM generates the Master Key (MK). When switching Key Store, a new MK is generated in the new Key Store. The existing DEKs are re-protected using this new MK and the old MK is deactivated.
Protegrity Soft HSM: The Protegrity Soft HSM is an internal Soft HSM bundled with the ESA. The Protegrity Soft HSM provides all the functionalities that are provided by an HSM. Using the Protegrity Soft HSM ensures that keys remain within the secure perimeter of the data security solution (ESA).
HSM: The Protegrity Data Security Platform provides you the flexibility, if needed, to switch to an HSM.
Ensure that the HSM supports the PKCS #11 interface.
For more information about switching from the Key Store, refer to the HSM Integration.
Cloud HSM: Cloud-hosted Hardware Security Module (Cloud HSM) service enables you to host encryption keys in a cloud-hosted HSM cluster. You can perform cryptographic operations using this service as well. Protegrity supports both Amazon Web Service (AWS) and Google Cloud Platform (GCP) Cloud HSM. The GCP console is used to define a project where keyrings, keys, and key versions can be created. You can use GCP Cloud HSM to ensure the same key life cycles as on-premise.
Warning: Ensure that the project location supports creating HSM level keys.
For more information about switching Protegrity Soft HSM to Cloud HSM and Configuring the Keystore with the AWS Customer Managed Keys, refer to the Key Management Service (KMS) Integration on the Cloud Platforms.
Feedback
Was this page helpful?