Key Management Web UI
Master Keys Web UI
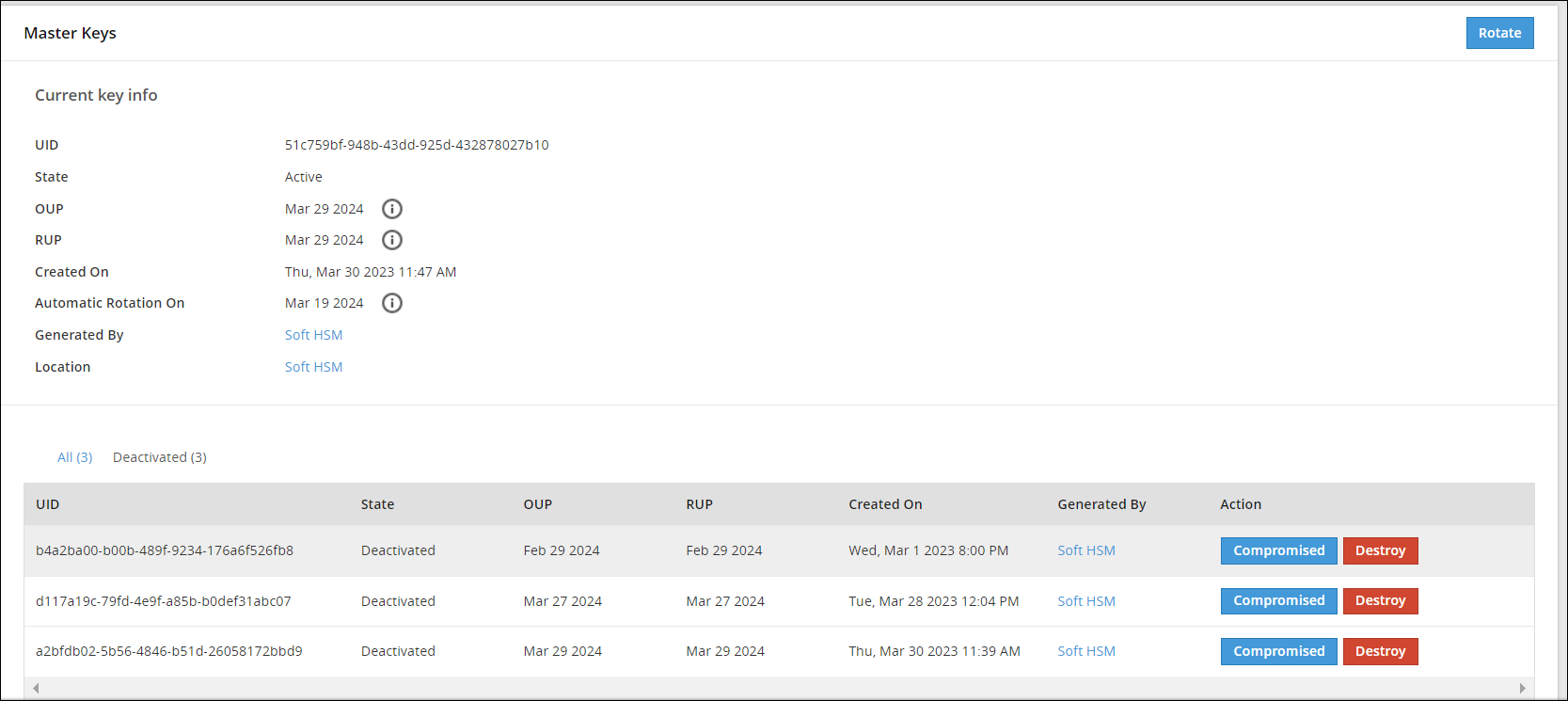
Information related to Master Keys, such as, state, timestamps for key creation and modification, and so on is available on the Master Keys Web UI.
The following image shows the Master Keys UI.
Repository Keys Web UI
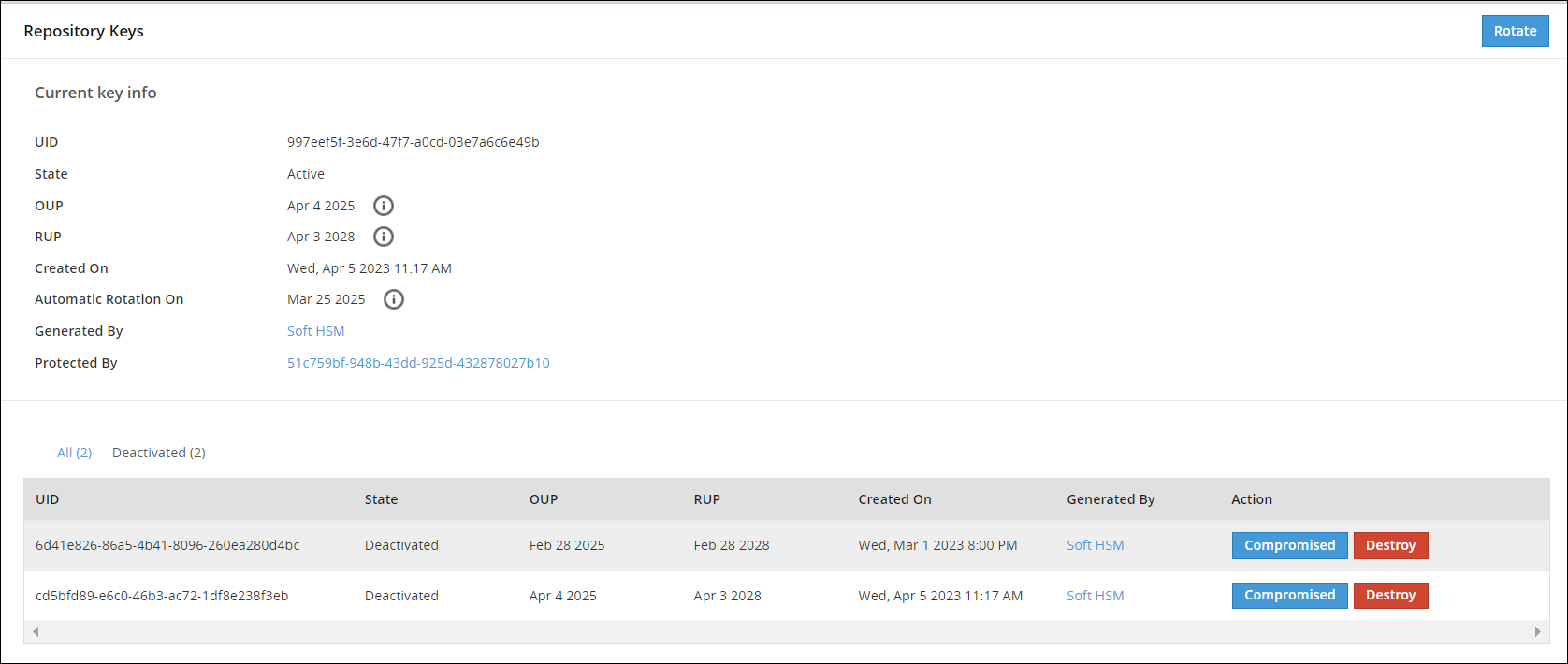
Information related to Repository keys, such as, state, timestamps for key creation and modification, and so on is available on the Repository Keys Web UI.
The following image shows the Repository Keys UI.
Data Store Keys Web UI
Information related to DSKs, such as, state, timestamps for key creation and modification, and so on is available on the Data Store Keys Web UI.
The following image shows the Data Store Keys UI.
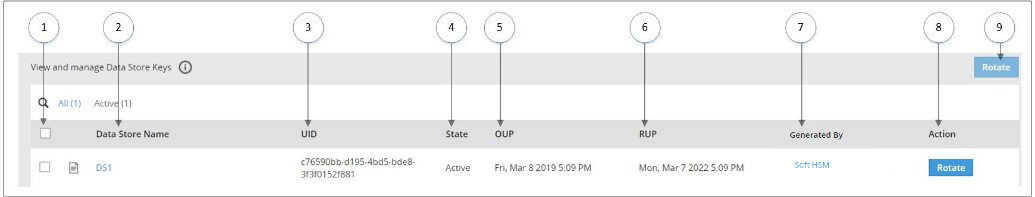
The options available as part of the UI are explained in the following table.
| No. | Option | Description |
|---|---|---|
| 1 | Select multiple Data Store | Select the check box to rotate multiple Data Stores at the same time. |
| 2 | Data Store Name | Click to view information related to Active DSK and older keys. |
| 3 | UID | Unique identifier of the key. |
| 4 | State | Current State of the DSK linked to the Data Store. |
| 5 | OUP | The period of time in the cryptoperiod of a symmetric key during which cryptographic protection may be applied to data. |
| 6 | RUP | The period of time during the cryptoperiod of a symmetric key during which the protected information is processed. |
| 7 | Generated By | Indicates which Key Store has the generated key. |
| 8 | Action | Rotate - Click to rotate the DSK for a Data Store Key. |
| 9 | Rotate | Click to rotate the DSK for multiple selected Data Store Keys. |
If you click the Data Store name, for example DS1, you can view detailed information about the active key and older keys.
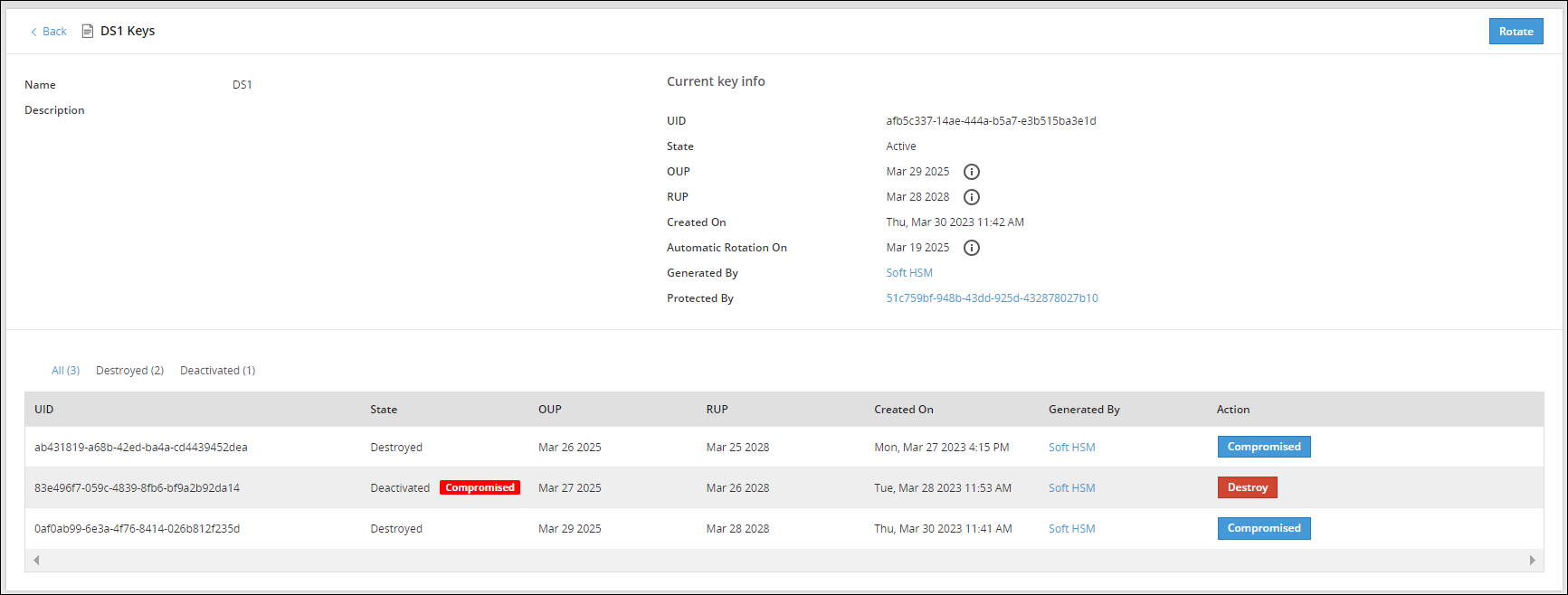
The Action column provides an option to change the state of a key to Destroyed or mark the key as Compromised. For more information about the options available for DSK states, refer to Changing Key States.
Signing Key Web UI
The Signing Key is used to add a signature to log records generated for each data protection operation. These signed log records are then sent from the Protector to the ESA. The Signing Key is used to identify if log records have been tampered with and that they are received from the required protection endpoint or Protector.
A single Signing Key is linked and deployed with all the data stores. At a time, only one Signing Key can be in the Active state.
The following image shows the Signing Keys UI.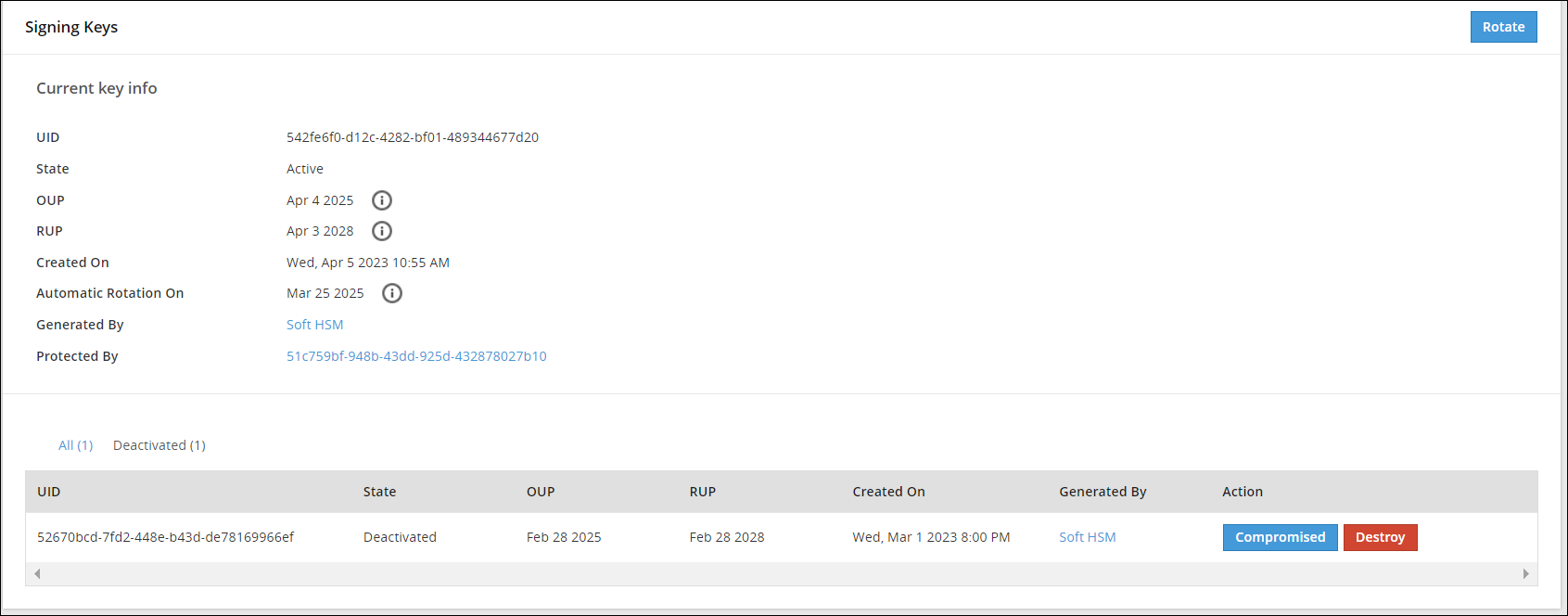
Data Element Keys Web UI
Information related to Data Element Keys, such as, state, OUP, RUP, and so on is available on the Data Element Keys Web UI.
The following image shows the Data Element Keys UI.
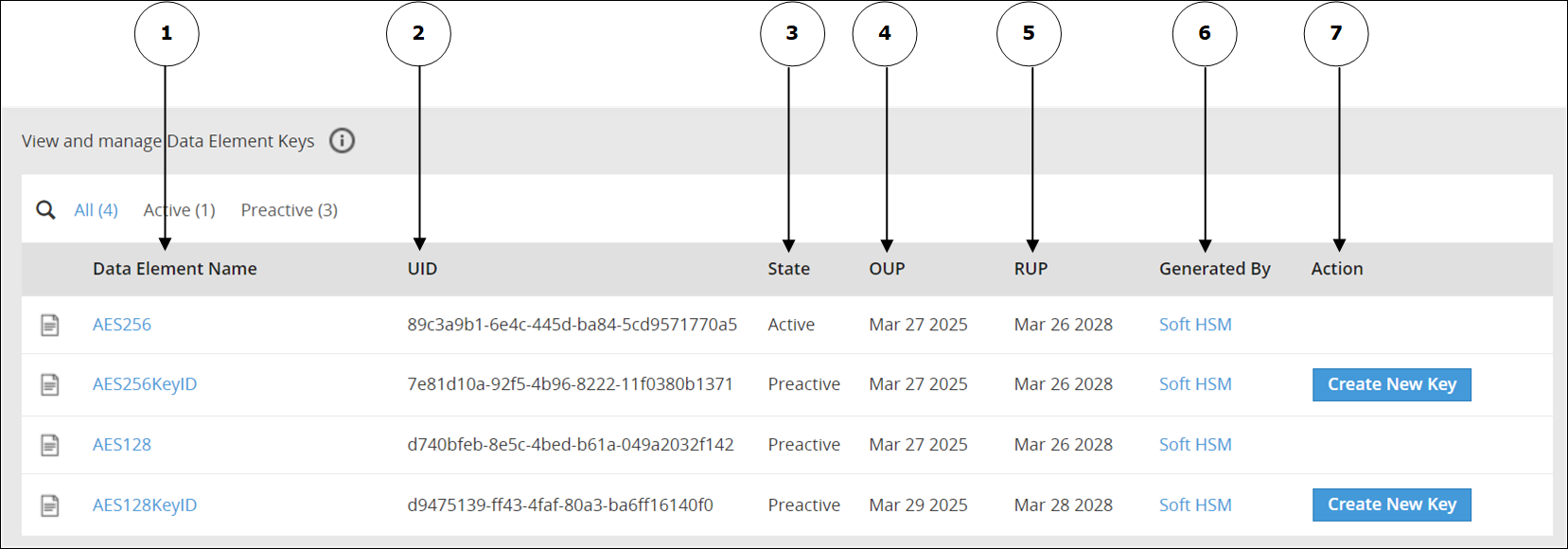
The options available as part of the UI are explained in the following table.
| No | Option | Description |
|---|---|---|
| 1 | Data Element Name | Click to view information related to the Active Data Element Key and older keys. |
| 2 | UID | Unique identifier of the key. |
| 3 | State | Current State of the Data Element Key linked to the Data Element. |
| 4 | OUP | The period of time in the cryptoperiod of a symmetric key during which cryptographic protection may be applied to data. |
| 5 | RUP | The period of time during the cryptoperiod of a symmetric key during which the protected information is processed. |
| 6 | Generated By | Indicates the source of key generation: - Soft HSM - The key has been generated by Protegrity Soft HSM. - Key Store - The Key Store used to generate the key. - Software - This option appears if you have generated the Data Element Key in an earlier version of the ESA before upgrading the ESA to v10.1.0. |
| 7 | Action | Create New Key: Click to create a new key. This option is available only if you have created a Data Element Key with a key ID. |
If you click the Data Element name, for example AeS256KeyID, then you can view detailed information about an active key and older keys.
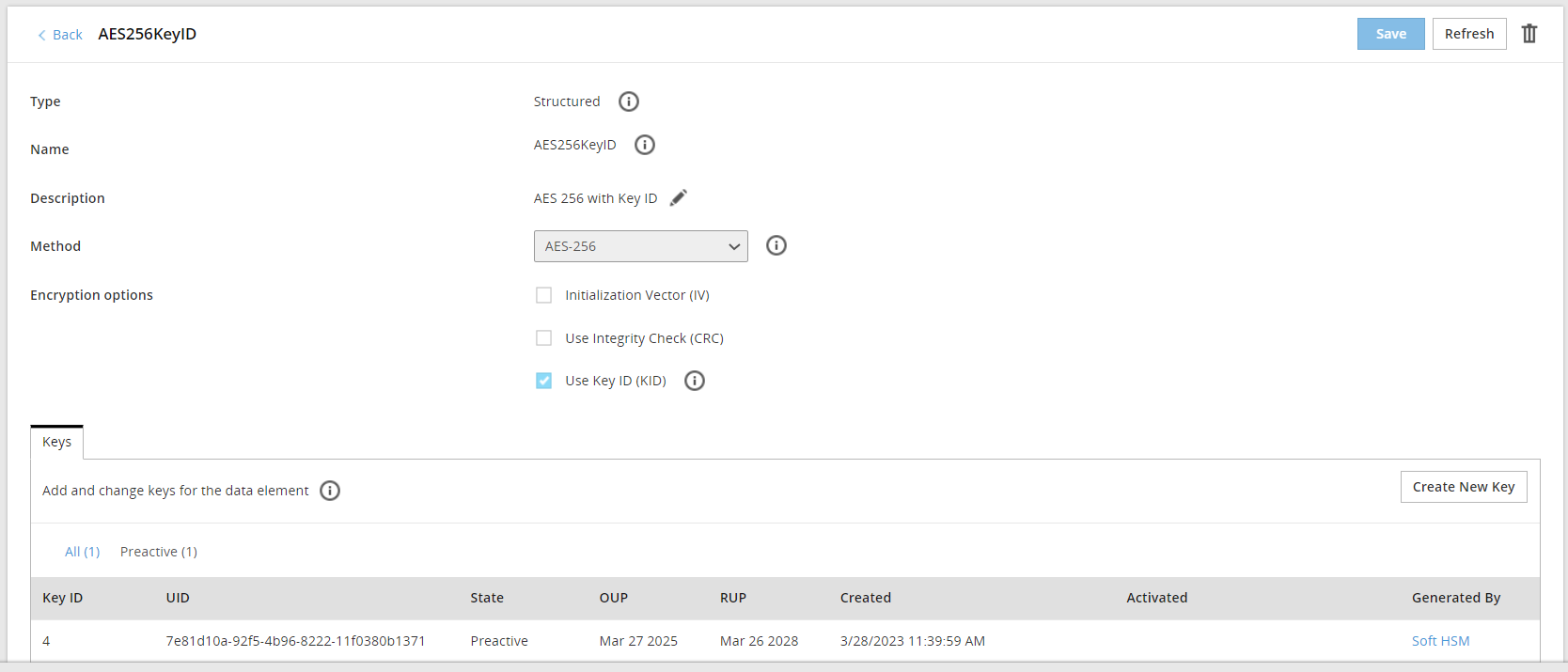
If key ID is enabled for a data element, then you click Create New Key to create a new key for the data element.
Important: Starting from the ESA v10.1.0, the Data Element Keys are generated by the active Key Store. When MK is rotated, all DEKs needs to be re-protected. As a result, if you are using too many keys, then your system might slow down in the following scenarios:
You are frequently rotating the keys.
You are using too many encryption data elements where the Key ID is enabled. This allows you to create multiple keys for the same encryption data element.
You are using too many data stores.
Your connection to the HSM is slow.
You can find out the total number of keys currently in use from the Keys area in the Policy Management Dashboard.
Feedback
Was this page helpful?