Working with Keys
Key rotation involves putting the new encryption key into active use. Key rotation can take place when the key is about to expire or when it needs to be deactivated due to malicious threats.
Master Key (MK), Repository Key (RK), Data Store Key (DSK), and Signing Key
The key rotation for KEKs and DEKs in the Protegrity Data Security Platform can be described as follows:
- The Master Key (MK), Repository Key (RK), Data Store Key (DSK), and Signing Key can be rotated using the ESA Web UI.
- The supported states for the MK, RK, DSK, and Signing Key are Active, Deactivated, Compromised, and Destroyed.
- When the ESA is installed, the MK, RK, and Signing Key are in the Active state.
- When the MK, RK, DSK, and Signing Key is rotated, the old key state changes from Active to Deactivated, while the new key becomes Active.
- The MK, RK, DSK, and Signing Key is set for automatic rotation ten days prior to the Originator Usage Period (OUP) expiration date by default.
- On the ESA Web UI, navigate to Key Management > Key Name to view the key details.
- The rotation for the MK, RK, DSK, and Signing Key from the ESA Web UI requires the user to be assigned with the KeyManager role.
Viewing the Key Information
You can view the MK,RK, DSK, and Signing Key information, such as, state, OUP, RUP,and other details using the Web UI. To view the key information:
- On the ESA Web UI, click Key Management > Required Key tab.
For example; if you select MK, the MK screen appears.
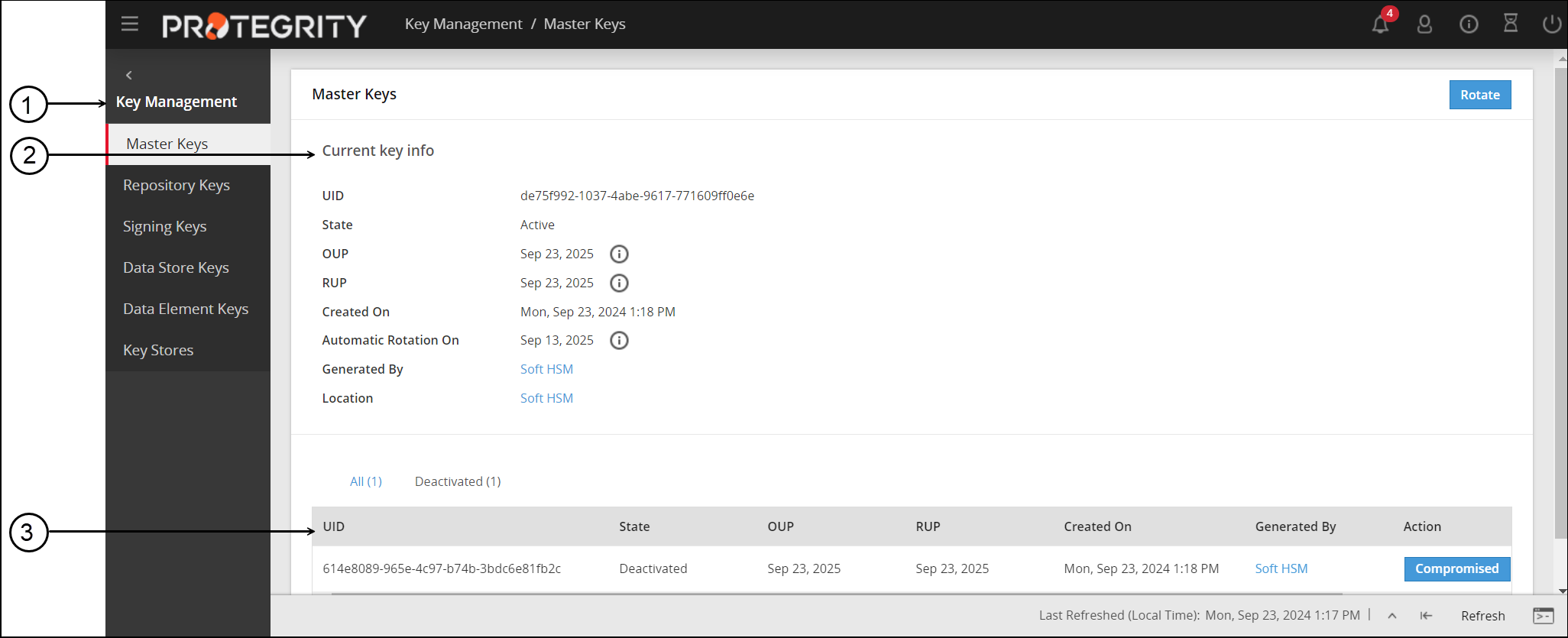
- In the Current key info section, view the current key information.
- The table displays the information related to the older Master Key.
You can rotate the MK, RK, DSK, and Signing Key by clicking the Rotate button.
Changing the Key States
The following table provides information about the possible key states for MK, RK, DSK, and Signing Key that you can change based on their current state.
Current Key State | Can change state to | State Change | |
State | Reason | ||
Active | Deactivated |
| Auto |
Deactivated | Compromised | Key is compromised. | Manual |
Destroyed | Organization requirement | Manual | |
In the Deactivated key state, you can -
- Click Compromised to mark the key as Compromised and display a Compromised label next to the state.
- Click Destroy to mark the key as Destroyed and display a Destroyed label next to the state.
Data Element Keys
Data elements can have key IDs associated with them. Key IDs are a way to correlate a data element with its encrypted data. When a data element is created, and if the protection method is key based, a unique Data Element Key is generated. This key is seen in the Key Management Web UI.
Information related to Data Element Keys, such as, state, OUP, RUP, and so on is available on the Data Element Keys Web UI.
To view information about the Data Element Key:
- On the ESA Web UI, click Key Management > Data Element Keys.
The View and manage Data Element Keys screen displays the list of data element keys. - Click a data element name, for example DE1. The Data Elements tab appears, which displays the current information about the Data Element Key.
- The table displays the information related to the older Data Element Keys.
Data Element Key States
This section describes the key states for the Data Element Keys.
The following table provides information about the possible key states for the Data Element Keys that you can change based on their current state.
Current Key State | Can change state to | State Change | |
State | Reason | ||
| Preactive | Active | Deploying a policy | Auto |
Active | Deactivated | Adding a new key to the data element.If you click the Data Element name, for example AES256KeyID, then you click Create New Key button to create a new key for the data element. | Auto |
When you create a new key, its state is set to Preactive state.
Key Cryptoperiod and States
Cryptoperiods can be defined as the time span for which the key remains available for use across an enterprise. Setting cryptoperiods ensures that the probability of key compromise by external threats is limited. Shorter cryptoperiods ensure that the strength of security is greater.
In the ESA, the Master Key, Repository Key, Signing Key, Data Store Key, and the Data Element Keys are governed by cryptoperiods. For these keys in the ESA, the validity is dictated by the Originator Usage Period (OUP) and the Recipient Usage Period (RUP). The OUP is the period until when the key can be used for protection, while the RUP is the period when the key can be used to unprotect only.
For keys in Protegrity, the following table provides the OUP and RUP information.
| Key Name | OUP | RUP |
|---|---|---|
| Master Key | 1 Year | 1 Year |
| Repository Key | <=2 Years | <=5 Years |
| Data Store Key | <=2 Years | <=5 Years |
| Signing Key | <=2 Years | <=5 Years |
| Data Element Key | <=2 Years | <=5 Years |
For more information about key states, refer to Changing Key States.
Feedback
Was this page helpful?